Claroty reports close to 800 ICS vulnerabilities, with 34 percent targeting IoT, IoMT, IT assets
Industrial cybersecurity company Claroty revealed that 797 industrial control system (ICS) vulnerabilities were published in the second half of last year, affecting 82 ICS vendors. Of these, 21 vendors are newly affected, had no recently published disclosures, and have equipment deployed across automation, manufacturing, and healthcare sectors.
ICS vulnerability disclosures recorded a 25 percent increase from the 637 vulnerabilities found in the first six months of last year. The present figure marked ‘a staggering 110% over the last four years,’ Claroty said in its fourth ‘Biannual ICS Risk & Vulnerability Report,’ released on Wednesday.
Out of the vulnerabilities disclosed, 34 percent affect IoT, Internet of Medical Things (IoMT), and IT assets, showing that organizations will merge operational technology (OT), IT, and IoT under converged security management. Therefore, asset owners and operators must have a thorough snapshot of their environments to manage vulnerabilities and reduce their exposure, it added.
Data shows an increase in ICS vulnerability disclosures and the number of vulnerabilities disclosed by internal research done by vendors. Coincidentally, the number of vendors doing internal research increased by 35 percent, demonstrating a maturing industry and discipline around vulnerability research, as vendors allocate more resources to the security of their products, it added.
Addressing ransomware concerns, Claroty said that the second half of last year ‘lacked a dramatic major incident.’ Critical infrastructure operators, in particular, must now consider whether ransomware attacks are a cover for a far deeper type of attack. As tensions deepened between Russia and Ukraine in January, destructive malware attacks were reported against government websites in Ukraine, it added.
“Using ransomware as a misdirection tactic, Ukrainian systems were instead infected with wiper malware that rendered hard drives on compromised machines useless. These types of misdirection attacks force defenders to spend needless time addressing what they believe to be a ransomware attack only to discover it’s a far more impactful intrusion,” the report added.
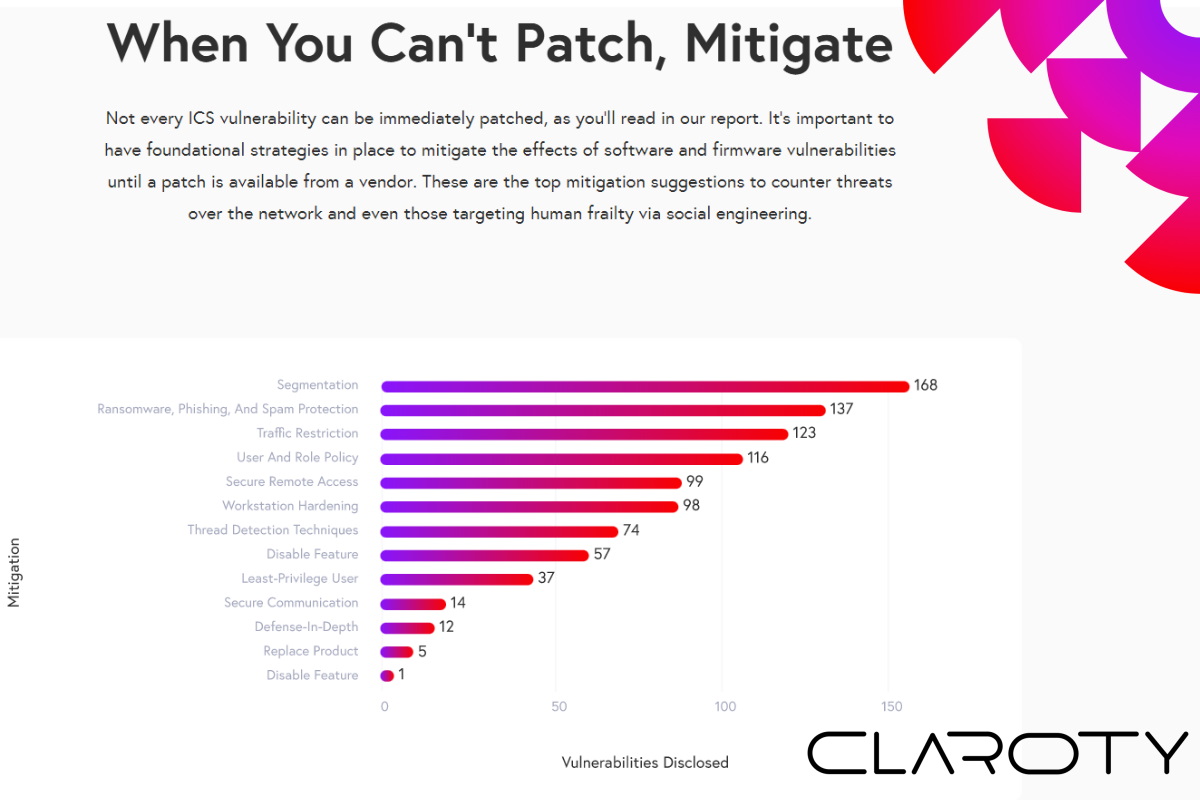
In 2022, asset owners and operators should be aware of these types of nation-state tactics and how kinetic conflicts can also spill online, Claroty said. As conflicts escalate, users should have adequate threat intelligence to keep abreast of tactics, techniques, and procedures used to target their infrastructure. Tightening firewall rules, blocking webmail to counter phishing attacks, backing up regularly, storing backup files offline and off-site, and securing OT project files are key strategies to remember as geopolitics enters cyberspace, it added.
With rising number of cyberattacks and need for industrial cyber resilience techniques and design principles be built in the shortest possible time, Amir Preminger, vice president of research at Claroty, told Industrial Cyber that “there are a number of things that industrial asset owners and operators can check for today—many of which should already be in place as best practices—to secure assets in a growing threat landscape and tense geopolitical climate.”
“This starts with limiting internet access to control systems and other devices and machines operating on an OT network, as these can be vulnerable entry points that attackers can leverage,” according to Preminger. “Staying up to date on threat intelligence from CISA, FBI and NSA is also important in order to build accurate cyber response plans and maintain business continuity even during a disruption,” he added.
In its latest report, Claroty detected that Siemens had the most reported vulnerabilities at 251, followed by Schneider Electric, Advantech, Delta Electronics, and Mitsubishi. “In 2H 2021, the majority of vulnerabilities affect software components, right, and given the comparative ease in patching software over firmware, defenders have the ability to properly prioritize patching within their environments,” it added.
For the second straight report, products fitting within Operations Management Level 3 of the Purdue Model — were the most affected by disclosed vulnerabilities, recording a total number of 217 vulnerabilities, or 27 percent, Claroty data revealed. “The software components at this level include the servers and databases at the core of the production workflow. Technology at this level also feeds data collected from field devices to higher-level business systems, or those operating in the cloud,” it added.
Products operating at the Basic Control (Level 1) and Supervisory Control (Level 2) levels were affected by 25 percent of the vulnerabilities disclosed in the last six months of last year, Claroty said. At the ‘Basic Control’ level are programmable logic controllers (PLCs), remote terminal units (RTUs), and other controllers that monitor Level 0 equipment like pumps, actuators, and sensors, while the ‘Supervisory Control’ level is made up of human-machine interfaces (HMIs), SCADA software, and other tools that monitor and act on Level 1 data.
“Within OT environments and critical infrastructure, operators and engineers need secure remote access to industrial assets in order to ensure process availability and safety,” Preminger highlighted. “Security practitioners should verify VPN versions, monitor remote connections and enforce granular access,” he added.
“And finally, since many control systems – especially Level 1 device firmware – are unable to be patched frequently, if at all, we recommend investing in segmentation, remote access protection, and better protection of the Operations Management and Supervisory Control levels, because they provide access to the Basic Control level, and eventually, the process itself,” he added.
Claroty’s Team82 research arm revealed that 63 percent of the vulnerabilities disclosed may be exploited remotely through a network attack vector, recording a slight increase of two percent from the previous six months.
The report said that the percentage of locally exploitable vulnerabilities dropped in the second half of last year to 31 percent. To exploit these vulnerabilities, an attacker would need a separate vector for network access to breach these flaws, with some of them requiring user interaction, such as phishing and spam to gain that initial network foothold. Ninety-four percent of operations management disclosures via a local attack vector require user interaction for exploitation, reinforcing the need for continuous education to prevent phishing attacks and stem the tide of destructive ransomware attacks, for example, it added.
Claroty said disclosing vulnerabilities is only one, albeit crucial, step in the vulnerability management process. Patches and mitigations are important to asset owners, operators, and security managers. With more connected devices coming online every day, an increasing number of systems are reachable and escalate the urgency for prompt fixes, it added.
Vulnerability remediation takes three forms – full remediation, where all affected products have a fix, partial remediation, where not all affected versions of products have a fix, and no remediation whatsoever. Claroty reported that 69 percent of vulnerabilities had full remediation, 15 percent had partial remediation, and 16 percent had no remediation.
Breaking down vulnerability remediation by software and firmware can help security practitioners create a strategic remediation and mitigation plan. Claroty said that 74 percent of fully remediated vulnerabilities are software-based. Defenders can prioritize patching within their environments given the comparative ease in patching software over firmware. It added that 62 percent of partially or ‘unremediated vulnerabilities,’ when exploited, could result in remote code execution or denial-of-service, the report added.
As for the firmware, Claroty found that in addition to the inability to update over time, fewer remediation solutions are available. “When firmware remediations exist (partial or full), Team82’s data shows they are largely for network devices, followed by Basic Control (Level 1), and IoT. This demonstrates that even in firmware, some prioritization of updates could happen because updating a network device, for example, a switch, is easier and likelier than upgrading a PLC or an RTU,” it added.
Claroty found that 87 percent of vulnerabilities are low complexity, indicating that they do not require any special conditions, and an attacker can expect repeatable success every time. Further, 70 percent do not require special privileges before successfully exploiting a vulnerability, and 64 percent of vulnerabilities require no user interaction.
Last week, another industrial cybersecurity company Dragos reported that it had assessed 1,703 ICS/OT common vulnerabilities and exposures (CVE) from various sources, including independent researchers, vendors, and ICS-CERT, recording more than twice as much as last year. It also identified three new threat activity groups that assessed motivation to target ICS/OT environments in 2021.










