Escalating threat landscape necessitates industrial secure remote access to safeguard digital infrastructure

Building remote access mechanisms across industrial environments can improve efficiency and reduce costs as technicians and engineers can troubleshoot and maintain equipment without physically being on-site. These processes have revolutionized the way industries operate by increasing accessibility and optimizing productivity, enabling engineers to monitor and troubleshoot equipment from any location, reducing downtime, and minimizing costs associated with travel. With secure remote access, technicians can easily diagnose problems in real-time, provide immediate solutions, and perform routine maintenance tasks without disrupting operations on-site.
Implementation of relevant security measures provides organizations with a strong defense against potential cyber threats and ensures the protection of digital assets. By utilizing a combination of security processes and solutions, companies can prevent unauthorized access to their systems and safeguard sensitive data from being compromised. This helps to maintain the confidentiality and integrity of information while building trust with customers and stakeholders who rely on the organization to keep their data safe. Overall, investing in robust security measures is a critical step for any organization to protect itself from the ever-evolving landscape of cyber threats.
Enhanced connectivity has ensured that remote connections into ICS (industrial control systems) are here to stay. Structurally, these remote connections into ICS should pass through the demilitarized zone (DMZ) between the IT and OT (operational technology) segments, as organizations work towards building their secure remote access architecture. Firewalls, authentication services, jump servers, and file servers all play crucial roles in conducting these connections securely.
In the first part of this two-part article, industrial cybersecurity experts address the need for secure remote access to industrial environments and assets, which seems more acute today than in the past. They also explore what has changed and what factors may be driving this trend. They also analyze the major risks/threats associated with remote industrial access.
Although remote access has been available for many years, many plant owners and operators seem to be only now becoming aware of the significant risks involved. In this part, the executives analyze why it has taken so long to recognize such potential dangers, and why now.

“Asset owners and operators, until recently, had limited awareness and understanding of the risks associated with remote access,” Jonathon Gordon, directing analyst at Takepoint Research, told Industrial Cyber. “They often adopted an ‘if it’s not broke, don’t fix it’ attitude, assuming that their existing practices were sufficient. As a result, they did not prioritize assessing the potential vulnerabilities of remote access. Their focus was primarily on other operational priorities, which contributed to a lack of attention towards evaluating and mitigating the risks associated with remote access,” he added.
Gordon highlighted that this has started to change due to the issues mentioned and high-profile security compromises in industrial environments that have received significant media attention. “These incidents have served as cautionary tales, emphasizing the need to address remote access vulnerabilities,” he added.

Over the last few years, industrial organizations have realized they are expanding the attack surface as they are increasing digitization, Ruben Lobo, director of product management at Cisco IoT, told Industrial Cyber. “Numerous news reports about malware intrusions or cyberattacks to industrial control systems have brought more focus on the risks. The war in Ukraine and the publicity of state-sponsored attacks also helped influence organizations to secure their industrial operations effectively,” he added.
“All our industrial customers have put OT cybersecurity at the top of their priority list. IT and SecOps teams have been asked to help operations secure their infrastructures,” according to Lobo. “Vulnerability management, network segmentation, and remote access are the topics they are focusing on to improve their security posture.”
Lobo added that many industries must also comply with strict security regulations such as CIRCIA in the U.S. or NIS in the EU. “These regulations mandate that critical infrastructures must report cyber incidents such as unauthorized access to systems. So there is now a regulatory incentive not only to being able to control and monitor remote access to industrial networks but also to store logs for reporting and forensic analysis.”

Remote access wasn’t widely perceived as a critical component of industrial environments and operations until 2020 when COVID forced many into working remotely, Brian Dunphy, vice president of product management at Claroty, told Industrial Cyber. “As a result, security wasn’t at the forefront of remote environments – industrial operators and leaders were just focusing on the quickest and easiest way to get employees remote network access to keep systems running. And for many organizations, these conditions led to existing and largely unsecured, IT-oriented solutions (such as VPN-based tools) being used for remote access to OT environments.”
Dunphy added that now, many understand the dangers of that approach, “as hackers have been targeting industrial environments via remote access attacks through vulnerable devices, compromised credentials, and more.”

The Colonial Pipeline attack in 2021 provided a highly visible example of the costs and negative consequences of an attack on critical infrastructure, Roman Arutyunov, co-founder and senior vice president of products at Xage Security, told Industrial Cyber. “This attack was reported to have cost millions of dollars not only in ransom payments to the attacker but in investigation costs and lost business, as the pipeline was shut down as a precautionary measure while the investigation was underway. It also caused massive panic – buying of gas up and down the East coast of the U.S.”
Arutyunov identifies that this was a wake-up call for critical infrastructure operators, and it led directly to the creation of new regulations by the TSA specifically regulating cybersecurity at oil and gas pipeline operators. “A series of high profile attacks spurring increasing Federal regulations, and the resulting barrage of news coverage have raised the profile of this topic considerably.”
Beyond that, the sheer volume of cyber attacks has gone up, and cyber attackers are constantly seeking new targets, Arutyunov said. “Attacker tools that start out being developed by more sophisticated groups gradually trickle down and become commoditized, available to less sophisticated cybercrime gangs. Somewhere along the line, cyber attackers turned their sights on critical infrastructure.”
At the same time, the massively increasing volume of operational assets in the field provided an increased attack surface, and increased leverage, for attackers to go after, according to Arutyunov. “Increasing political tensions globally may have also contributed to increased targeting of critical infrastructure, as indicated by the recent People’s Republic of China-sponsored attackers dubbed Volt Typhoon discovered ‘living-off-the-land’ in U.S. critical infrastructure systems.”
Last October, SANS identified ‘secure remote access’ as one of five critical ICS cybersecurity controls. The experts examine whether remote access security is among the top five ICS security controls. If so, they explore why it is so important.
“Unsecured remote access to industrial environments leaves the entire system vulnerable to unauthorized entry and manipulation,” according to Gordon. “It can grant malicious actors direct access to an organization’s most valuable assets, essentially bypassing other security measures that may be in place. Without proper security measures in place, remote access becomes a significant risk factor that can potentially undermine the overall security of the industrial environment.”
Arutyunov confirmed that secure remote access is of utmost importance today. “Most cyber attacks start by abusing a compromised credential to establish a remote connection so that the attacker can conduct command and control from afar. After that, compromised credentials are also often used for lateral movement, to spread malware, and expand the attacker’s footprint. Using secure remote access methods cuts the attacker off early in the process before their attack can really get started.”
“This is why preventive cybersecurity needs to be the first priority for critical infrastructure operators,” according to Arutyunov. “Using an identity-centric approach to securing remote access takes away one of the attacker’s most powerful, and most commonly used tools: the compromised credential. Controlling not only user access but machine-to-machine access, with a zero trust, least privilege approach can prevent initial intrusion and lateral movement, blocking attacks at the source before they get started.”
The experts also provide readers with best practices to consider when securing industrial remote access.
Securing remote access in industrial environments is indeed a continuous journey, Gordon said.
TP Research has developed a maturity model that assists asset owners, operators, and other stakeholders to align with one another and with cybersecurity frameworks they have adopted and conduct I-SRA (industrial secure remote access) gap analyses. It is designed to identify the current I-SRA implementation status (starting point) and the desired outcome of the project. The template should be modified to suit the organization. Like all undertakings in cyber/technology, the I-SRA market will continue to evolve. Therefore, organizations should periodically evaluate their current status using the template.
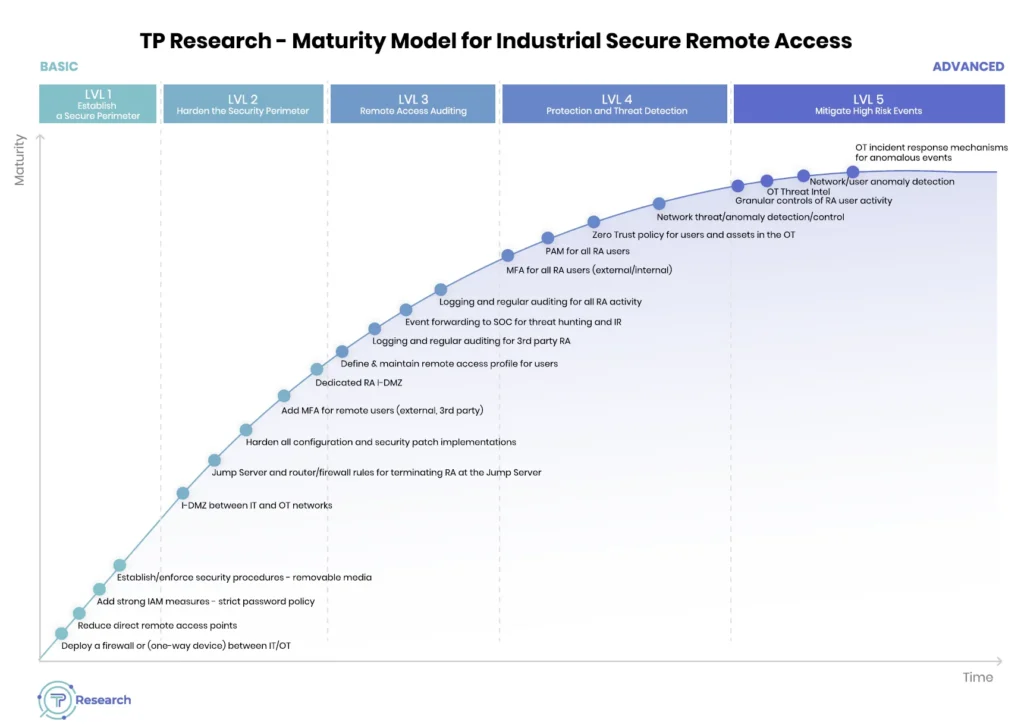
“TP Research recognizes this and offers a valuable approach to help customers assess their current state and define their desired future state,” according to Gordon. “By utilizing a maturity model, companies can identify their current level of technological capabilities, the skills and knowledge of their personnel, and the efficiency of their processes related to remote access security.”
“This mapping of the current state allows industrial enterprises to determine the necessary measures and improvements needed to bridge the gap between their current state and their desired level of security,” Gordon added. “This approach helps organizations develop a roadmap and implement the appropriate technologies, train their staff, and establish effective processes to enhance remote access security.”
Secure remote access must be a central part of any OT security strategy, according to Lobo. “There is a technical and a sourcing component to it. When buying machines or any OT assets, the operations team should specify that remote access will be managed by their IT teams through their own solutions and procedures. If vendors require dedicated cellular gateways, the IT team should be made aware in order to control their configurations and monitor their activities,” he added.
“From a technical perspective, industrial organizations need to implement a process to enable and control remote access that is both secured and scalable,” Lobo said. “It can become very complex to create access rights quickly when operations need them, to revoke them easily, to record sessions to set responsibilities in case of issues, to manage firewall exceptions, all that across multiple distributed locations.”
Lobo added that most remote access solutions available today rely on DMZ jumpboxes, transferring to end-users the burden of exposing IP addresses from Level-2 assets to the industrial DMZ. “This requires advanced IT expertise to configure and makes it very difficult to comply with industrial workflows where OT teams often need immediate access to devices but don’t have the skills (or time) to configure jumpboxes.”
“Multifactor authentication (MFA) should be mandatory to safeguard network security in case credentials get stolen,” Lobo highlighted. “Verifying the security posture of the remote user workstation should also be considered to ensure no malware or malicious traffic get their way in via authorized connections.”
He also suggests that fine-grained security policies should be defined together with the OT team, including the definition of which protocols can be used, when would remote access be allowed, which devices can be accessed by whom, etc. “IT and OT teams must be closely collaborating to define the right policies and implement a solution that OT users will be willing to adopt.”
Dunphy indicated that the most commonly recommended best practices when it comes to securing remote access to industrial environments include granular role and policy-based access, monitoring user access and action, enforcing two-factor secure authentication, and secure file transfer.
“Remote access solutions should have the ability to define and enforce extremely granular access controls for industrial assets at multiple levels and geographic locations, down to enabling access for a specific user to a specific asset to perform a specific task during a set time window,” according to Dunphy. “In addition, this can be further protected by requiring an explicit supervisor approval per access request. Visibility and control over third-party and employee access before, during, and after a remote session takes place are essential for investigation and response to malicious activity.”
Dunphy added that two-factor authentication is a must to limit shared accounts and stolen credentials. “Often users need the ability to transfer files to the operational environment – opportunities for malicious code to be inserted into the secure environment. Operational environments need the ability to enforce AV scanning for all files prior to upload,” he added.
Arutyunov said that there are many best practices to consider when securing industrial remote access. “The foundation of these best practices is a zero-trust approach. Users and machines should have the absolute least privilege necessary to conduct their function. This requires an asset-centric approach that controls every interaction between users, machines, data, and applications with granular, identity-based policies. Multi-IAM policy orchestration and enforcement across OT, IT, and cloud is critical when securing industrial remote access. OT and IT environments are often required to have separate identity and access management instances, but orchestrating policy across these systems provides the organization with a greater ability to protect every asset.
He added that implementing multi-factor authentication at every layer, from cloud to IT to DMZ to OT is another important step in building a defense-in-depth strategy. “One of the most significant security risks in many industrial organizations is colloquially known as ‘RDP-and-Free.’ This refers to a situation in which someone who accesses your OT environment via RDP has blanket access to every asset in the zone. This is the opposite of a zero-trust approach and introduces many risks. Look for IAM tools that enforce MFA at every layer and down to the individual device level.”
Arutyunov also reminded ensuring access control works offline is also important. “Technology has to work without the internet at operational sites in remote locations. If any aspect of your identity infrastructure requires an internet connection, it won’t hold up to the loss of internet at many OT sites. In addition, your remote access solution should log every interaction. Tracking every interaction taken by a specific identity or set of credentials is required to secure assets and ensure identities are not misused.
Lastly, Arutyunov said to remember that machines have identities, too. “Every device is a potential vector for an attacker to move laterally across the segment and spread malware. Identity-based access management needs to identify and control the access privileges of machines to each other and users to machines,” he concluded.










