Data breach costs for critical infrastructure sector exceed $5 million, as time ‘new currency’ in cybersecurity
New data from IBM Security disclosed that the global average cost of a data breach reached US$4.45 million in 2023, recording an all-time high and a 15 percent increase over the last three years. While data breach costs for critical infrastructure industries exceed $5 million as the cost of data breach climbed to a new high, the healthcare sector reported the highest costs for the 13th year in a row. Smaller organizations also faced considerably higher data breach costs than last year.
In its annual ‘Cost of a Data Breach’ report, IBM said that while data breach costs continued to rise, report participants were almost equally split on whether they plan to increase security investments because of a data breach. Detection and escalation costs jumped 42 percent over this same time frame, representing the highest portion of breach costs, and indicating a shift towards more complex breach investigations. It also found that businesses are divided in how they plan to handle the increasing cost and frequency of data breaches.
The 2023 Cost of a Data Breach Report is based on an in-depth analysis of real-world data breaches experienced by 553 organizations globally between March 2022 and March 2023. The research, sponsored and analyzed by IBM Security, was conducted by Ponemon Institute and has been published for 18 consecutive years.
IBM reported that across industries, healthcare reported the highest costs for the 13th year in a row. “Healthcare continues to experience the highest data breach costs of all industries, increasing from USD 10.10 million in 2022 to USD 10.93 million in 2023—an increase of 8.2%. Over the past three years, the average cost of a data breach in healthcare has grown 53.3%, increasing more than USD 3 million compared to the average cost of USD 7.13 million in 2020. Healthcare faces high levels of industry regulation and is considered critical infrastructure by the US government. Since the start of the COVID-19 pandemic, the industry has seen notably higher average data breach costs.”
The report added that the top five most costly industries underwent some changes from last year’s rankings. “Technology dropped out of the top five while the industrial sector was added, showing a 5.8% increase as it moved from the seventh-highest to the fifth. According to IBM threat intelligence, manufacturing is the industry most commonly targeted by cybercriminals.”
“Time is the new currency in cybersecurity both for the defenders and the attackers. As the report shows, early detection and fast response can significantly reduce the impact of a breach,” Chris McCurdy, general manager for worldwide IBM Security Services, said in a media statement. “Security teams must focus on where adversaries are the most successful and concentrate their efforts on stopping them before they achieve their goals. Investments in threat detection and response approaches that accelerate defenders’ speed and efficiency – such as AI and automation – are crucial to shifting this balance.”
The top areas identified for additional investments included incident response (IR) planning and testing, employee training, and threat detection and response technologies. The study found that while 95 percent of studied organizations have experienced more than one breach, breached organizations were more likely to pass incident costs onto consumers at 57 percent than to increase security investments at 51 percent.
The report disclosed that cost savings were achieved by organizations with high levels of IR planning and testing. “In addition to being a priority investment for organizations, IR planning, and testing emerged as a highly effective tactic for containing the cost of a data breach. Organizations with high levels of IR planning and testing saved USD 1.49 million compared to those with low levels.”
IBM reported that only one-third of companies discovered the data breach through their own security teams, compared to 27 percent that was disclosed by an attacker, highlighting a need for better threat detection. “67% of breaches were reported by a benign third party or by the attackers themselves. When attackers disclosed a breach, it cost organizations nearly USD 1 million more compared to internal detection,” it added.
The report also identified that in 2023, organizations with more than 5,000 employees saw the average cost of a data breach decrease compared to 2022. “On the other hand, those with 5,000 or fewer employees saw considerable increases in the average cost of a data breach. Organizations with fewer than 500 employees reported that the average impact of a data breach increased from USD 2.92 million to USD 3.31 million or 13.4%. Those with 500–1,000 employees saw an increase of 21.4%, from USD 2.71 million to USD 3.29 million. In the 1,001–5,000 employee range, the average cost of a data breach increased from USD 4.06 million to USD 4.87 million, rising nearly 20%.”
Released Monday, the report also revealed the percentage of breaches that involved data stored in the cloud—public, private, or multiple environments. “Cloud environments were frequent targets for cyber attackers in 2023. Attackers often gained access to multiple environments, with 39% of breaches spanning multiple environments and incurring a higher-than-average cost of USD 4.75 million,” it added.
The report also said that AI and automation had the biggest impact on the speed of breach identification and containment for studied organizations. Organizations with extensive use of both AI and automation experienced a data breach lifecycle that was 108 days shorter compared to studied organizations that have not deployed these technologies (214 days versus 322 days). These organizations also saw, on average, nearly $1.8 million lower data breach costs than organizations that didn’t deploy these technologies – the biggest cost saver identified in the report.
At the same time, adversaries have reduced the average time to complete a ransomware attack. Ransomware victims in the study that involved law enforcement saved $470,000 in average costs of a breach compared to those that chose not to involve law enforcement. Despite these potential savings, 37 percent of ransomware victims studied did not involve law enforcement in a ransomware attack. Furthermore, with nearly 40 percent of studied organizations yet to deploy security AI and automation, there is still considerable opportunity for organizations to boost detection and response speeds.
IBM also found additional costs experienced by organizations that didn’t involve law enforcement in a ransomware attack. This year’s research shows that excluding law enforcement from ransomware, incidents led to higher costs. While 63 percent of respondents said they involved law enforcement, the 37 percent that didn’t, also paid 9.6 percent more and experienced a 33-day longer breach lifecycle.
The report also identified an increase in data breach costs for organizations that had high levels of security system complexity. Organizations that reported low or no security system complexity experienced an average data breach cost of $3.84 million in 2023. Those with high levels of security system complexity reported an average cost of USD 5.28 million, representing an increase of 31.6 percent.
Additionally, the report found an average cost difference of $1.02 million between breaches that took more than 200 days to find and resolve, and those that took less than 200 days. “Time to identify and contain breaches—known as the breach lifecycle—continues to be integral to the overall financial impact. Breaches with identification and containment times under 200 days cost organizations USD 3.93 million. Those over 200 days cost USD 4.95 million—a difference of 23%,” it added.
When it came to ransomware and destructive attacks, IBM reported that these accounted for 24 percent and 25 percent of malicious attacks, respectively. Nearly one-quarter of attacks involved ransomware. Destructive attacks that left systems inoperable accounted for one out of every four attacks, and another 24 percent involved ransomware. Business partner and software supply chain attacks accounted for 15 percent and 12 percent of attacks, respectively.
“Ransomware attack costs increased significantly,” IBM said. “At USD 5.13 million, the average cost of a ransomware attack in the 2023 report increased 13% from the average cost of USD 4.54 million in the 2022 report. At USD 5.24 million, the average cost of a destructive attack in the 2023 report also increased 2.3% from the average cost of USD 5.12 million in the 2022 report.”
Another interesting fact that IBM reported was that organizations that involved law enforcement saw significant time and cost savings. 37 percent of ransomware victims opted not to involve law enforcement to help contain a ransomware breach, but those that did experience a less costly ransomware breach overall. The average cost of a ransomware breach was $5.11 million when law enforcement wasn’t involved and $4.64 million when law enforcement was involved, for a difference of 9.6 percent or $470,000.
The report also found that law enforcement helped shorten the time to identify and contain ransomware breaches. “Total time to identify and contain a ransomware breach was 11.4% or 33 days shorter with law enforcement involvement, at 273 days in total compared to 306 days. The mean time to contain a ransomware breach was 63 days or 23.8% shorter with law enforcement involvement compared to 80 days without. It’s clear that involving law enforcement can help reduce the cost and duration of a ransomware breach,” IBM said.
“A business partner supply chain compromise cost 11.8% more and took 12.8% longer to identify and contain than other breach types. The cost of a data breach due to a business partner supply chain compromise averaged USD 4.76 million, which was USD 530,000 or 11.8% higher than the USD 4.23 million average cost of a data breach that was due to another cause,” IBM disclosed. “Organizations took an average of 233 days to identify and 74 days to contain a business partner supply chain compromise, for a total lifecycle of 307 days. That average lifecycle was 37 days or 12.8% longer than the average lifecycle of 270 days for data breaches attributed to another cause.”
When it came to software supply chain compromises, IBM reported that it cost 8.3 percent more and took 8.9 percent longer to identify and contain than other breach types. “The cost of a data breach due to a software supply chain compromise averaged USD 4.63 million, which was USD 370,000 or 8.3% higher than the USD 4.26 million average cost of a data breach that was due to another cause. A breach due to a software supply chain compromise had an 8.9% longer lifecycle, at 294 days compared to 269 than data breaches due to other causes.”
Although a supply chain compromise originating from within the software supply chain is less costly than one originating from a business partner, both still cost more and take longer than the average data breach, the report added.
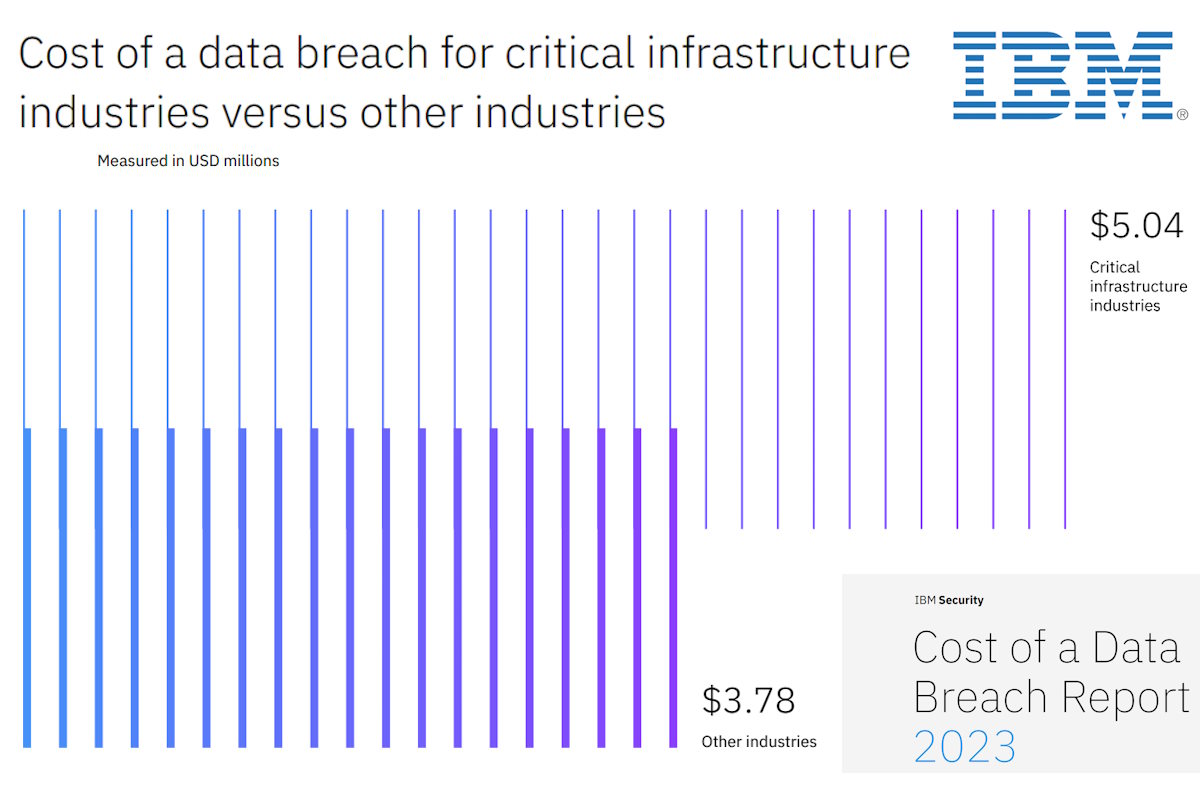
Critical infrastructure organizations included those in the financial services, industrial, technology, energy, transportation, communication, healthcare, education and public sector industries, IBM reported. “These organizations incurred data breach costs that were USD 1.26 million higher than the average cost of USD 3.78 million for organizations in other industries, a difference of 28.6%. This USD 5.04 million value also reflects a 4.6% increase of USD 4.82 million over the 2022 reported average cost of a data breach for critical infrastructure industries.”
To help reduce the cost of a data breach, IBM Security suggests that organizations include successful security approaches that are associated with reduced costs and lower times to identify and contain breaches. Among these measures, the report lists building security into every stage of software development and deployment—and testing regularly; modernizing data protection across hybrid cloud; using security AI and automation to increase speed and accuracy; and strengthening resiliency by knowing the attack surface and practicing IR.
In February, IBM Security reported that the number of industrial control system (ICS) vulnerabilities discovered in 2022 fell to 457 for the first time in two years, down from 715 in 2021 and 472 in 2020. One explanation could be found in ICS lifecycles and how they are managed and patched in general. It also revealed that the manufacturing sector was the most targeted in 2022, accounting for 58 percent of incidents that X-Force assisted in resolving.










