RA Group hackers target US, South Korean organizations using leaked Babuk ransomware source code
Researchers from Cisco Talos recently discovered a new ransomware actor called RA Group that has been operating since at least April 22, 2023. The team assesses with high confidence that RA Group is leveraging leaked Babuk ransomware source code and is ‘swiftly expanding’ its operations. The group is said to have to date compromised three organizations in the U.S. and one in South Korea across several business verticals, including manufacturing, wealth management, insurance providers, and pharmaceuticals.
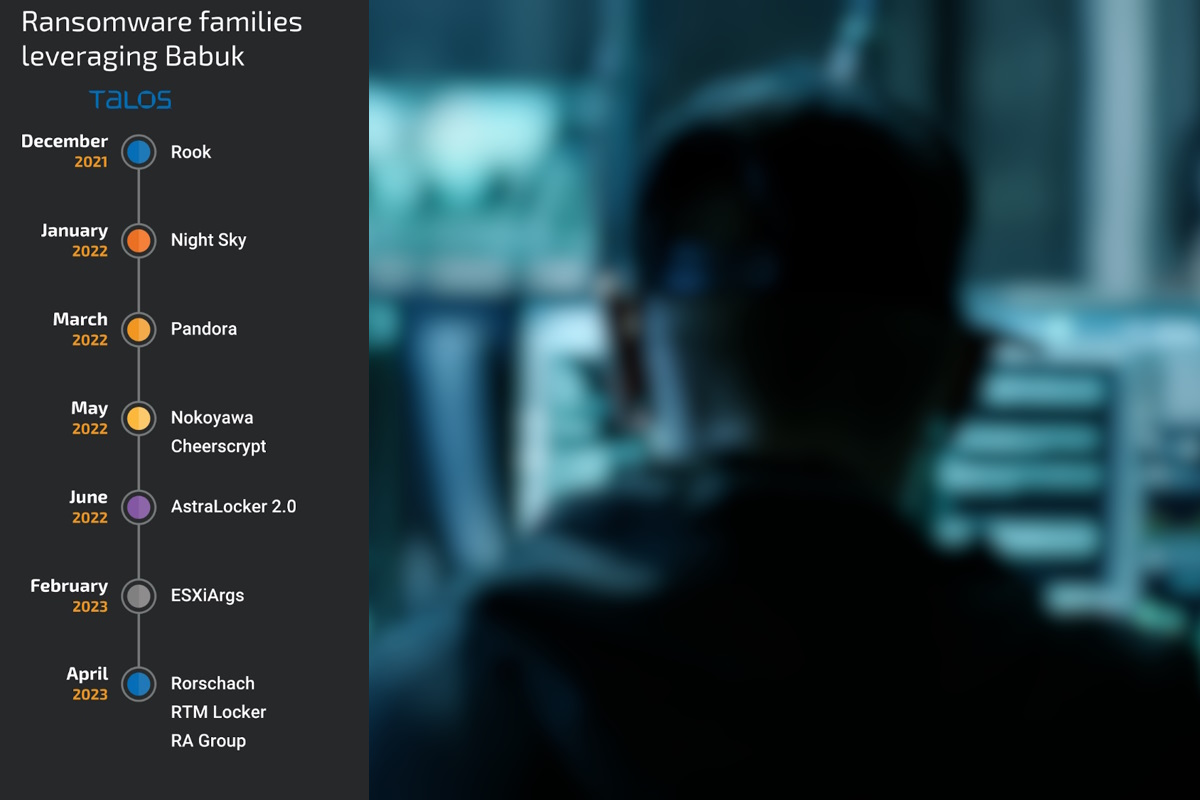
“Talos recently discovered a new ransomware actor, RA Group, who emerged in April 2023 and seems to be using leaked Babuk source code in its attacks,” Chetan Raghuprasad, wrote in a Cisco Talos blog post on Monday. “After an alleged member of the Babuk group leaked the full source code of its ransomware in September 2021, various ransomware families have emerged leveraging the leaked Babuk code. Talos has compiled a timeline of these attacks conducted by different actors using ransomware families that branched off the leaked source code.”
Raghuprasad outlined that the group is launching double extortion attacks. “Like other ransomware actors, RA Group also operates a data leak site in which they threaten to publish the data exfiltrated from victims who fail to contact them within a specified time or do not meet their ransom demands. This form of double extortion increases the chances that a victim will pay the requested ransom,” he added.
“This actor is expanding its operations at a fast pace. RA Group launched their data leak site on April 22, 2023, and on April 27, we observed the first batch of victims, three in total, followed by another one on April 28,” Raghuprasad disclosed. “We also observed the actor making cosmetic changes to their leak site after disclosing the victim’s details, confirming they are in the early stages of their operation.”
Furthermore, “in their leak site, RA Group discloses the name of the victim’s organization, a list of their exfiltrated data and the total size, and the victim’s official URL, which is typical among other ransomware groups’ leak sites. The RA Group is also selling the victim’s exfiltrated data on their leak site by hosting the victims’ leaked data on a secured Tor site. RA Group also provides URLs to download the full file listings of the victim’s data on their leak site,” the post added.
“RA Group uses customized ransom notes, including the victim’s name and a unique link to download the exfiltration proofs,” according to Raghuprasad. “After activating the ransomware executable on the victim’s machine, the actor drops the ransom note file called ‘How To Restore Your Files[dot]txt.’ Based on the ransom notes we analyzed, if the victim fails to contact the actors within three days, the group leaks the victim’s files. The victims can confirm the exfiltration of their information by downloading a file using the gofile[dot]io link in the ransom note,” he added.
The Cisco Talos post also added that RA Group deploys their ransomware with a built-in ransom note specifically written to each victim with their name on it, a common practice among ransomware groups. However, it is unusual that RA Group names the victim in the executable, as well.
Analysis by Cisco Talos researchers shows that RA Group’s ransomware sample is written in C++ and was compiled on April 23, 2023. “It contains the same mutex name as the Babuk ransomware, supporting our high-confidence assessment that RA Group built their ransomware using Babuk’s leaked source code,” the post added.
Raghuprasad detailed that the RA Group’s ransomware executable uses the cryptography scheme with curve25519 and eSTREAM cipher hc-128 algorithm for encryption. “This process encrypts only a certain part of the source file’s contents, not the entire file. It uses WinAPI CryptGenRandom to generate cryptographically random bytes used as a private key for each victim. After encrypting the files, the ransomware appends the file extension ‘.GAGUP’ to the encrypted files on the victim’s machine,” he added.
The ransomware deletes the contents of the victim machine’s Recycle Bin with the API SHEmptyRecyclebinA, Raghuprasad said. “It deletes the volume shadow copy by executing the local Windows binary vssadmin.exe, an administrative tool used to manipulate shadow copies.”
The Cisco Talos post also highlighted that the ransomware enumerates every logical drive on the victim’s machine by comparing logical drive letters with the list of drive letter strings in the binary and mounts the identified drives to perform the encryption process. “RA Group’s malware enumerates the network shares and available network resources on the victim’s machine using the APIs NetShareEnum, WNetOpenEnumW, and WNetEnumResourceW to encrypt files on the remotely mapped drives of other machines or servers,” it added.
Raghuprasad identified that the ransomware does not encrypt all files and folders. “These files and folders are necessary for the system to work properly and to allow the victims to download the qTox application and contact RA group operators using the qTox ID provided on the ransom note,” he added.
Providing comments on what these attacks could mean for these critical sectors, Joshua Corman, vice president of cyber safety strategy at Claroty, said in an emailed statement that the recent attacks on multiple critical infrastructure systems like manufacturing and pharmaceuticals prove there’s still work that needs to be done in protecting access to our most vital resources. “Critical infrastructure owners and operators also tend to be the most target-rich, but cyber-poor.”
“While the primary impact of the malicious attacks by RA Ransomware Group was data theft, as we’ve seen elsewhere, malicious intent is not a prerequisite to harm,” according to Corman. “Follow-on attacks could be even more devastating if they lead to protracted downtime or cause damage to cyber-physical systems – which could dramatically impact civilians who rely on these systems. Protecting the nation’s critical infrastructure requires a re-balancing of responsibilities across public-private collaboration to close the current gaps and potential risk to the U.S. national security.”
Corman added that the recent White House National Cybersecurity Strategy addresses this. “It’s time we all step up to protect the systems and services we rely on every day from being easy targets.”
In recent times, ransomware attacks on critical infrastructure have been rapidly increasing and pose a greater threat to operational technology (OT) assets and control systems. In recent years, the quantity and range of ransomware infections targeting industrial organizations have significantly increased, exemplified by cases, such as EKANS and the Colonial Pipeline attacks. At the same time, the proliferation of such attacks is reaching new heights of sophistication, with escalating demands for payment skyrocketing into the tens of millions of dollars, posing financial and operational risks to industrial organizations globally.










