Russia-backed Sandworm hackers disrupt Ukraine power grid using novel OT attack techniques
Mandiant researchers detailed Thursday that late last year it responded to a disruptive cyber-physical incident in which the Russia-linked threat actor Sandworm targeted a Ukrainian critical infrastructure organization. The incident was a multi-event cyber attack that leveraged a novel technique for impacting industrial control systems (ICS) / operational technology (OT). The Sandworm hackers initially used OT-level living off the land (LotL) techniques to likely trip the victim’s substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine. Sandworm later conducted a second disruptive event by deploying a new variant of CADDYWIPER in the victim’s IT environment.
Mandiant researchers reported that the Sandworm hackers then proceeded to carry out a second disruptive event by introducing a new variant of CADDYWIPER into the victim’s IT environment. These findings highlight the sophistication and evolving tactics of cyber threat actors, underscoring the need for robust cybersecurity measures to protect critical infrastructure organizations.
Mandiant detailed that the intrusion began on or before June 2022 and culminated in two disruptive events on Oct. 10 and 12, 2022. “While we were unable to identify the initial access vector into the IT environment, Sandworm gained access to the OT environment through a hypervisor that hosted a supervisory control and data acquisition (SCADA) management instance for the victim’s substation environment. Based on evidence of lateral movement, the attacker potentially had access to the SCADA system for up to three months,” it added.
The researchers added that two days following the OT activity, the Sandworm hackers deployed a new variant of CADDYWIPER throughout the IT environment. “This CADDYWIPER variant, compiled in October 2022, contains some minor functionality improvements that allow threat actors to resolve functions at runtime. We have observed CADDYWIPER deployed across several verticals in Ukraine, including the government and financial sectors, throughout Russia’s invasion of Ukraine.”
“This attack represents the latest evolution in Russia’s cyber-physical attack capability, which has been increasingly visible since Russia’s invasion of Ukraine,” Mandiant researchers said in the blog post. “The techniques leveraged during the incident suggest a growing maturity of Russia’s offensive OT arsenal, including an ability to recognize novel OT threat vectors, develop new capabilities, and leverage different types of OT infrastructure to execute attacks. By using LotL techniques, the actor likely decreased the time and resources required to conduct its cyber-physical attack.”
They added that while Mandiant was unable to determine the initial intrusion point, “our analysis suggests the OT component of this attack may have been developed in as little as two months. This indicates that the threat actor is likely capable of quickly developing similar capabilities against other OT systems from different original equipment manufacturers (OEMs) leveraged across the world.”
The researchers also outlined that the Sandworm hackers deployed CADDYWIPER in this operation via two Group Policy Objects (GPO) from a Domain Controller using TANKTRAP. “TANKTRAP is a utility written in PowerShell that utilizes Windows group policy to spread and launch a wiper. We have observed TANKTRAP being used with other disruptive tools including NEARMISS, SDELETE, PARTYTICKET, and CADDYWIPER. These group policies contained instructions to copy a file from a server to the local hard drive and to schedule a task to run the copied file at a particular time,” they added.
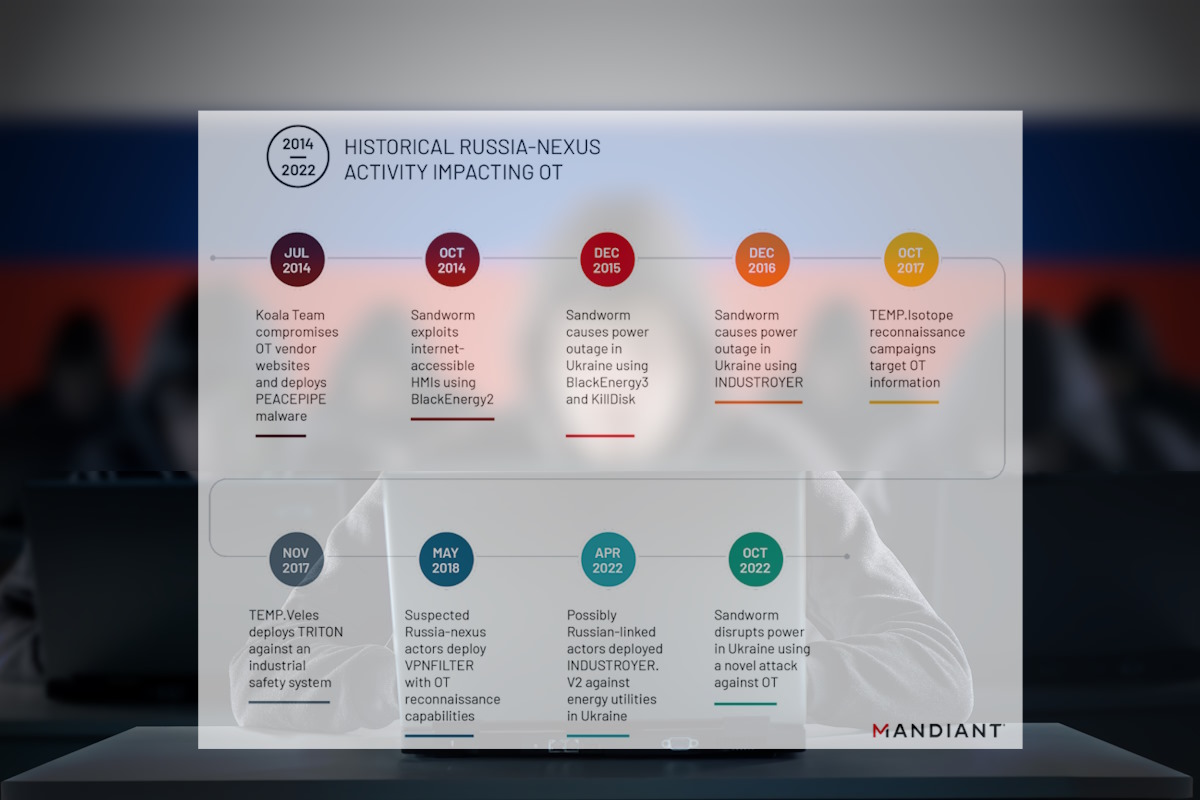
Mandiant said that it initially tracked this activity as UNC3810 before merging the cluster with Sandworm. “Sandworm is a full-spectrum threat actor that has carried out espionage, influence, and attack operations in support of Russia’s Main Intelligence Directorate (GRU) since at least 2009,” the researchers disclosed. “The group’s long-standing center focus has been Ukraine, where it has carried out a campaign of disruptive and destructive attacks over the past decade using wiper malware, including during Russia’s re-invasion in 2022.”
Beyond Ukraine, the researchers added that the Sandworm hackers continue to sustain espionage operations that are global in scope and illustrative of the Russian military’s far-reaching ambitions and interests in other regions. “Government indictments have linked the group to the Main Center for Special Technologies (also known as GTsST and Military Unit 74455). Given Sandworm’s global threat activity and novel OT capabilities, we urge OT asset owners to take action to mitigate this threat.”
The researchers detailed that Sandworm’s substation attack reveals notable insights into Russia’s continued investment in OT-oriented offensive cyber capabilities and overall approach to attacking OT systems. “This incident and last year’s INDUSTROYER.V2 incident both show efforts to streamline OT attack capabilities through simplified deployment features. We observed the same efforts in our analysis of a series of documents detailing project requirements to enhance Russian offensive cyber capabilities,” they added.
“By comparison, the INDUSTROYER.V2 incidents lacked many of those same disruptive components and the malware did not feature the wiper module from the original INDUSTROYER,” Mandiant added. “Likewise, Sandworm’s activity in the OT network appears streamlined to only executing unauthorized ICS command messages, with the wiper activity limited to the IT environment. While this shift likely reflects the increased tempo of wartime cyber operations, it also reveals the GRU’s priority objectives in OT attacks.”
Furthermore, Sandworm’s use of a native LotL binary (LotLBin) to disrupt an OT environment shows a significant shift in techniques. “Using tools that are more lightweight and generic than those observed in prior OT incidents, the actor likely decreased the time and resources required to conduct a cyber-physical attack. LotLBin techniques also make it difficult for defenders to detect threat activity as they need to not only remain vigilant for new files introduced to their environments but also for modifications to files already present within their installed OT applications and services.”
“While we lack sufficient evidence to assess a possible link, we note that the timing of the attack overlaps with Russian kinetic operations,” the researchers disclosed. “Sandworm potentially developed the disruptive capability as early as three weeks prior to the OT event, suggesting the attacker may have been waiting for a specific moment to deploy the capability. The eventual execution of the attack coincided with the start of a multi-day set of coordinated missile strikes on critical infrastructure across several Ukrainian cities, including the city in which the victim was located.”
In September, the Computer Emergency Response Team of Ukraine (CERT-UA) recorded a targeted cyber attack against a critical energy infrastructure facility in the country. The advisory added that the described activity is carried out by the Russian state-sponsored APT28 hacker group. The agency confirmed that they were able to prevent any intrusion.










