The Essential Guide to the IEC 62443 industrial cybersecurity standards

Industrial cybersecurity standards have evolved to provide the critical infrastructure agencies and industrial sectors with established guidelines and best practices within their OT (operational technology) and industrial control systems (ICS) environments. Standards, such as the IEC 62443 series and the NERC reliability regulations, work towards delivering a holistic approach to organizational frameworks, having matured from a consensus among stakeholders within the community, based on their expertise and experience over time.
Standards provide a level playing field to industry stakeholders, representing years of trial and error while offering practical application of knowledge and improving communications. They lead to creating a set of characteristics or qualities that describe features of a product, process, service, interface or material, and help achieve operational excellence by improving performance, lowering maintenance costs, decreasing downtime, boosting operability, and saving money.
Industrial organizations are now better poised to adopt the commonly accepted standards and focus their attention on carrying out their critical functions and processes. These industrial cybersecurity standards have evolved from consensus among technical experts, including their instructions, guidelines, rules, or definitions, and then deployed across industrial and manufacturing domains.
Over a series, Industrial Cyber will provide industry stakeholders with detailed guides on the various industrial cybersecurity standards currently available to the industrial, government sector, and critical infrastructure domains. The first part of this series presents an extensive review of the IEC 62443 cybersecurity standards.
The ISA/IEC 62443 standards
The ISA/IEC 62443 standards are the most comprehensive and exhaustive industrial cybersecurity standards available to the industrial and manufacturing sector, which addresses the cybersecurity challenges of industrial automation and control systems (IACS) and OT environments. The IACS technologies are central to critical infrastructure and OT environments. Apart from geographically dispersed operations, IACS includes control systems used in manufacturing and processing plants and facilities, including those found across the utilities, pipelines, petroleum production, and distribution facilities.
The IEC 62443 standards received a significant boost in November 2021 when the International Society of Automation (ISA) and the ISA Global Cybersecurity Alliance (ISAGCA) announced that the International Electrotechnical Commission (IEC) recognized the industrial cybersecurity standards series as having ‘horizontal’ capability.
Traditionally associated with OT environments, the latest acceptance will ensure that the IEC 62443 standards are considered horizontal or base. As a result, the series is technology-independent and can be applied across technical areas, thereby widening the reach of these standards and delivering consensus-based cybersecurity merit for automation and control system applications. It also further drives consensus among asset owners and operators to focus their efforts on collaboration and advancement of the series of standards to meet current demands in various areas such as IIoT, sensor-level security, and supply chain risks.
The IEC 62443 standards provide cybersecurity reference architectures, direction for security processes, requirements, technology, controls, security acceptance/factory testing, product development, security lifecycles, and a cybersecurity management system (CSMS). It also lays down relevant policies and procedures that organizations could bring into their frameworks and provides periodic reviews and specific requirements to instill best practices. Using these IEC 62443 standards, organizations can better cope with the rising cyber threats and attacks that infiltrate the control system and the work processes, countermeasures, and employees.
Industrial and manufacturing companies can deploy the ISA/IEC 62443 regulations to provide a comprehensive organizational framework with adequate cybersecurity controls and measures. In addition, using the internationally recognized line of standards allows asset owners and operators to design acceptable and complete technical solutions with integrated security measures and capabilities for their infrastructure.
The IEC 62443 standards are adopted to structure organizational IACS security maturity and posture while providing a range of criteria for security products, programs, and service providers. The recommendation from the IEC 62443 is also regularly supplemented with technical reports covering specific technological situations and solutions.
By adopting the ISA/IEC 62443 series of standards as a base, asset owners and operators will have enhanced exposure. In addition, automation system suppliers will certify their products for a broader range of applications, using a standard set of conformance specifications based on the series. The deployment of the standards enables organizations to focus on adopting security as part of the operations lifecycle while delivering compliance across various aspects of the standards across their supply chains better. It also provides cybersecurity in operational risk-management profiles.
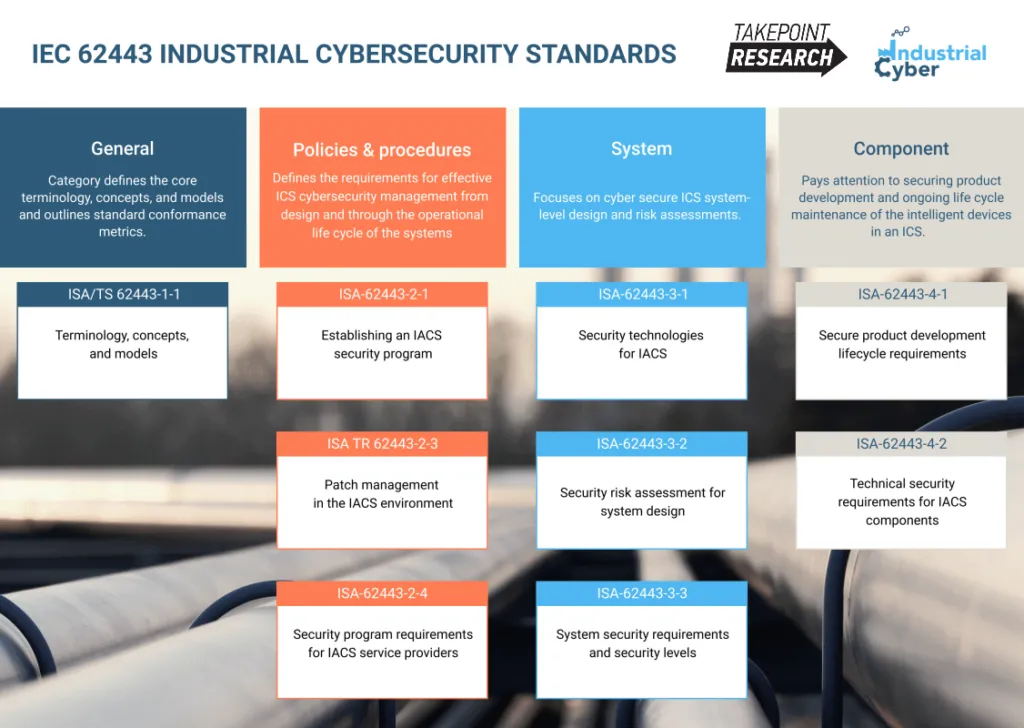
The IEC 62443 series comprises nine standards, technical reports (TR), and technical specifications (TS). The nine standards can be classified into four groups – General, Policies and Procedures, System, and Component.
The first two groups describe concepts, use cases, policies, and procedures associated with ICS security. In contrast, the two latter groups focus on the technical requirements for networks and system components.
- The ‘General’ category defines the core terminology, concepts, and models and outlines standard conformance metrics.
- ‘Policies and Procedures’ defines the requirements for effective ICS cybersecurity management from design and through the operational life cycle of the systems
- ‘System’ focuses on cyber secure ICS system-level design and risk assessments.
- ‘Component’ pays attention to securing product development and ongoing life cycle maintenance of the intelligent devices in an ICS. The standards body regularly consults IACS security experts to maintain relevant guidance applicable to all industrial and critical infrastructure sectors.
Breakdown of the IEC 62443 standards
The IEC 62443 series of standards is organized into four parts:
General
Part 1 covers topics that are common to the entire series:
- 1-1 (TS): Terminology, concepts, and models
Policies and procedures
Part 2 focuses on methods and processes associated with IACS security:
- 2-1: Establishing an IACS security program
- 2-3 (TR): Patch management in the IACS environment
- 2-4: Security program requirements for IACS service providers
System
Part 3 is about requirements at the system level:
- 3-1: Security technologies for IACS
- 3-2: Security risk assessment for system design
- 3-3: System security requirements and security levels
Components and requirements
Part 4 provides detailed requirements for IACS products:
- 4-1: Secure product development lifecycle requirements
- 4-2: Technical security requirements for IACS components
The IEC/TS 62443-1-1 outlines the terminology, concepts, and models for IACS security and establishes the basis for the remaining standards in the IEC 62443 series. Published in July 2009, the IEC 62443-1-1 has been prepared by IEC technical committee 65. It establishes the basis for the remaining standards in the IEC 62443 series.
Released in November 2010, the 62443-2-1 is concerned with establishing an industrial automation and control system security program that profiles the elements necessary to initiate a cybersecurity management system (CSMS) for IACS environments while providing recommendations on how to develop those elements. The standard uses the broad definition and scope of what constitutes an IACS described in IEC/TS 62443-1-1.
The IEC TR 62443-2-3 covers security for IACS product suppliers that have established and are now maintaining an IACS patch management program. The standard recommends a defined format for distributing information about security patches from asset owners to IACS product suppliers, a definition of some of the activities associated with the development of the patch information by IACS product suppliers, and deployment and installation of the patches by asset owners. The exchange format and actions are defined for use in security-related patches. However, it may also be applicable for non-security-related patches or updates.
The IEC 62443-2-4 concerns security program requirements for IACS service providers that highlight requirements for security capabilities for IACS service providers to offer to the asset owner during integration and maintenance activities of an automation solution. It has been developed by IEC Technical Committee 65 in collaboration with the International Instrumentation Users Association, referred to as the WIB from its original and now obsolete Dutch name, and ISA 99 committee members.
The IEC 62443-3-1 handles security technologies for IACS, delivering a current assessment of various cybersecurity tools, mitigation countermeasures, and technologies that may effectively apply to the modern electronically based IACSs regulating and monitoring numerous industries and critical infrastructure environments.
It describes several categories of control system-centric cybersecurity technologies, the types of products available in those categories, advantages, and disadvantages of using those products in the automated IACS environments, relative to the expected threats and known cyber vulnerabilities, along with the preliminary recommendations and guidance for using these cybersecurity technology products and/or countermeasures.
The IEC 62443-3-2 puts in place requirements for defining a system under consideration (SUC) for an IACS and its associated networks, partitioning the SUC into zones and conduits, assessing the risk for each zone and conduit, and establishing the technical measure security level targets (SL-T) for each zone and conduit. It also documents the security requirements needed to design, implement, operate and maintain adequate technical security measures. SL-T refers to the desired level of security for zones and conduits in a particular automation solution.
Risk management of the IACS starts with a proposed design based on company standards and practices and/or recognized and generally accepted good engineering practices (RAGAGEP). It also calls for understanding how to identify vulnerabilities, threats, consequences of a successful attack, rank risks, and implement mitigation measures to lower risks to tolerable levels. The standard itself is considered a RAGAGEP.
The ISA 62443-3-2 standard is based on the understanding that IACS security is a matter of risk management. Each IACS would present a different risk to an organization depending upon the threats it is exposed to, the likelihood of those threats arising, the inherent vulnerabilities within the system, and the subsequent consequences if the system were to be compromised. Further, each organization that owns and operates an IACS has its risk tolerance.
The IEC 62443-3-3 defines detailed technical control system requirements (SRs) linked with the seven foundational requirements (FRs) described in IEC 62443-1-1, including outlining the requirements for control system capability security levels SL-C (control system). These requirements would be used by various stakeholders of the IACS community, along with the defined zones and conduits for the SuC while developing the appropriate control system target SL, SL-T(control system), for a specific asset. The demands can be applied to integrated IACS, either implemented in-house by end-users or provided as an automation solution by a service provider.
The IEC 62443-4-1 specifies the process requirements for the secure development of products used in IACS. It defines secure development life-cycle (SDL) requirements related to cybersecurity for products intended for use in the industrial automation and control systems environment. It guides on meeting the requirements described for each element. The lifecycle description includes security requirements definition, secure design, secure implementation, including coding guidelines, verification and validation, defect management, patch management, and product end-of-life. These requirements can be applied to new or existing processes for developing, maintaining, and retiring hardware, software, or firmware.
The IEC 62443-4-2 provides detailed technical control system component requirements (CRs) associated with the seven FRs described in IEC TS 62443-1-1. These components include defining the requirements for control system capability security levels and their components, SL-C (component). Defining security capability levels for the control system component is the goal and objective of this document as opposed to SL-T or achieved SLs (SL-A), which are out of scope.
Frequently Asked Questions about IEC 62443 standards
- What are the cybersecurity standards?
Cybersecurity standards seek to bring industrial organizations a common framework for operators of OT (operational technology) and industrial control systems (ICS) networks through requirements, controls, and best practices. Standards deliver a holistic approach as they evolve from consensus among technical experts, their instructions, guidelines, rules, or definitions used across the industry to design, manufacture, install, test, certify, maintain and repair electrical and electronic devices and systems.
With the ISA/IEC 62443 standards, organizations get the opportunity to recognize what is most valuable within their environment, improve asset visibility, identify those that require more protection, and detect vulnerabilities. In addition, the adoption of standards in the industry helps improve communication and deliver practical application of expert knowledge considering years of experience.
Standards help organizations achieve operational excellence by improving performance, reducing operational downtime, boosting operability, bringing down maintenance costs, and ultimately saving money.
- How do I get IEC 62443 certified?
The ISA industrial cybersecurity training courses and knowledge-based certificate recognition program are based on the ISA/IEC 62443 series of automation cybersecurity standards and a key component of government cybersecurity plans. The schedule covers the complete lifecycle of IACS assessment, design, implementation, operations, and maintenance. Targeted at professionals involved in IT and control system security roles, it helps these executives develop a command of industrial cybersecurity terminology and an in-depth understanding of the implications of the ISA/IEC 62443 series of standards.
ISA certification and certificate programs offer a standards-based learning approach to critical topics within the automation industry. The hands-on, expert-led industrial cybersecurity courses leverage real-world equipment supported by industry vendors to increase professional recognition and validate specific knowledge areas.
The certificate programs provide security professionals with education, knowledge, and experience with an objective, third-party skill level assessment. Using an OT focus rather than an IT focus, ISA’s training provides cybersecurity engineers and technical professionals with the ability to identify vulnerabilities and protect systems from cybersecurity attacks.
- Security professionals can take one or all of ISA’s four exams and get an opportunity to be certified on the standards collection’s core concepts that include fundamentals, risk assessment, design, and maintenance. Completing all four core concepts gives the professional a designation of ‘ISA/IEC Cybersecurity Expert.’
- Vendors have an option to certify their products as IEC 62443 compliant for various security levels. These measures will help to strengthen the nature of products deployed in the OT and ICS environments.
- Asset owners can initiate and take steps to certify their sites or systems concerning the IEC 62443 standards. Furthermore, any anomaly can be immediately detected and addressed to strengthen the network.
- Evolution of the ISA/IEC 62443 standards
Published by the International Organization for Standardization (ISO), in partnership with the IEC, the IEC 62443 standards are a consensus-based series of automation cybersecurity standards. The IEC 62443 standards are based on the ISO 27001 (ISO/IEC 27001), which is an international standard focused on information security. In November 2021, these IEC standards were accepted as horizontal or base standards, ensuring technology independence and applicability across technical areas.
Developed by the Industrial Automation and Control System Security Committee (ISA99) of the ISA and adopted by the IEC, the IEC 62443 standards undertake meeting the current and future security requirements of the IACS throughout their lifecycle. The initial set of standards specific to the industrial cybersecurity sector was created in 2007 at the initiative of the ISA’s 99 committee.
ISA joined forces with the IEC in 2010 in the run-up to the combined standard ISA/IEC 62443 that integrates the former ISA-99 documents. These standards and technical reports were initially developed for the industrial process sector but have since been applied to building automation, medical devices, and transportation.
The ISA99 standards development committee aligned industrial cybersecurity experts from across the globe to develop ISA standards on IACS security. The focal point of the committee was to improve confidentiality, integrity, and availability of components or systems used for manufacturing or control and provide criteria for procuring and implementing secure control systems.
- How many security levels have been defined in OT security architecture as per IEC 62443?
One of the built-in features of the IEC 62443 standards is the security levels (SL) used to evaluate the cybersecurity risks to each OT and ICS system. This capability provides both industrial organizations and asset owners and operators with the ability to understand their assets, how they work within the infrastructure, identify potential security loopholes, and address these security gaps before an adversary identifies and breaches them.
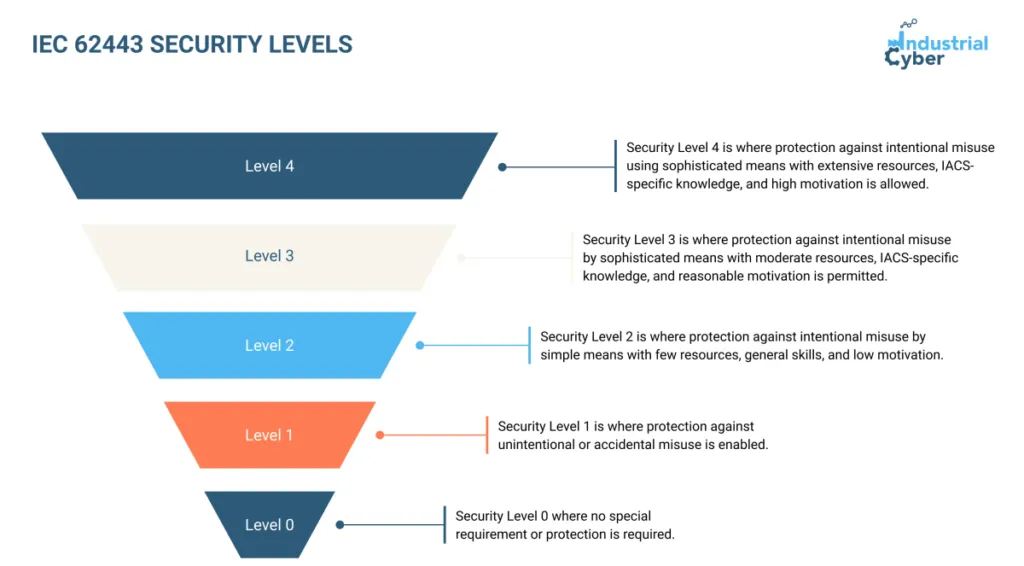
There are five Security Level grades, ranging from 0 to 4, with SL 0 identified as the minimum level of risk and SL 4 as the maximum or ‘most vulnerable’ level. This model calls for SL 4 requiring more significant compliance measures when compared to SL 0. The different ranks indicate the resistance against other classes of attackers.
To meet the security requirements of each security level, it is critical for the industrial system to have suitable protection for uptime, safety, and intellectual property. Therefore, industrial stakeholders operating within the industrial ecosystem can take advantage of clear expectations from asset owners and operators, systems integrators, equipment and service providers, and regulators.
The Security Levels are:
- Security Level 0 is where no special requirement or protection is required.
- Security Level 1 is where protection against unintentional or accidental misuse is enabled.
- Security Level 2 is where protection against intentional misuse by simple means with few resources, general skills, and low motivation.
- Security Level 3 is where protection against intentional misuse by sophisticated means with moderate resources, IACS-specific knowledge, and reasonable motivation is permitted.
- Security Level 4 is where protection against intentional misuse using sophisticated means with extensive resources, IACS-specific knowledge, and high motivation is allowed.
Conclusion
While the IEC 62443 industrial cybersecurity standards have many virtues and benefits, industrial stakeholders may find that the actual implementation on the ground comes with its fair share of challenges, as well. For instance, increasing system security can result in the need to upgrade older ICS equipment and purchase new cybersecurity appliances. In addition, required expenditure and implementation complexity will increase with the targeted security level.
Some of the standards are also not entirely complete. Others are in the process of being updated, and some others are yet to be published. In addition, the IEC 62443 standard is of extensive scope and content. At a total length of over 800 pages so far and more specifications coming soon, the industrial ecosystem must dedicate a significant amount of time and effort to read and understand the complete standard for proper implementation.










