Claroty’s Team82 reveals critical vulnerabilities in Unitronics UniStream devices, prompting vendor updates
Researchers from Claroty’s Team82 disclosed the presence of critical hardware vulnerabilities in Unitronics UniStream integrated PLC/HMI products, leading the vendor to update the product line. The vulnerabilities could allow an attacker to bypass authentication and enable remote code execution on devices directly connected to the internet.
Unitronics collaborated with the researchers to rectify identified vulnerabilities in a recent update. The company advises its users to update UniStream OS to version 1.35.47 or newer and has issued an advisory. Previous attacks targeting Unitronics’ Vision series of programmable logic controllers (PLCs) were disclosed in November. UniStream PLCs integrate HMI (Human-Machine Interface) features with advanced control capabilities, offering a versatile solution for industrial automation.
Recently, the PLCs were compromised in high-profile attacks against Israeli and American water treatment facilities. The vendor addressed the vulnerabilities used in those attacks.
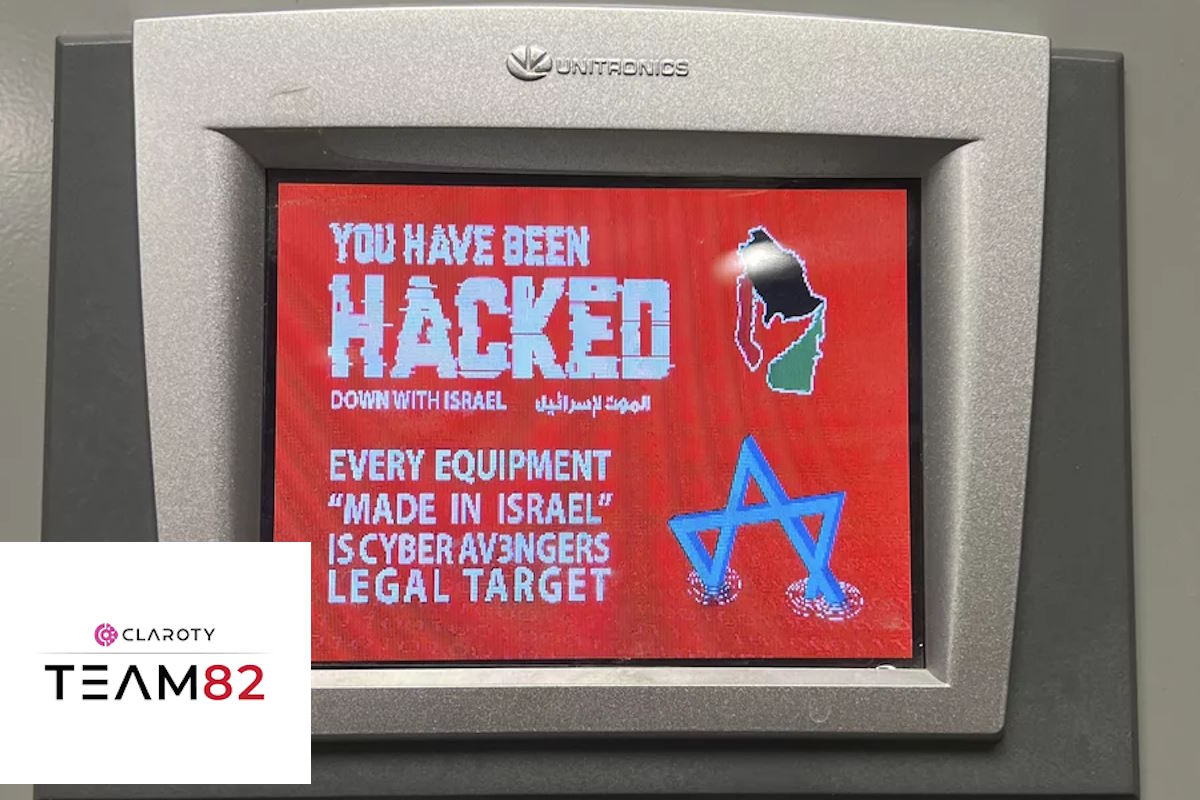
A group known as the CyberAv3ngers claimed responsibility for these attacks and singled out that all technology built in Israel was in their crosshairs. A compromised Unitronics V570 PLC/HMI at the municipal Water Authority of Alquippa was defaced, indicating that the attackers at least had access to the device.
The attack prompted the Cybersecurity Infrastructure and Security Agency (CISA) to publish an advisory warning users to change default passwords on Unitronics products, close ports directly exposing these devices to the internet, and secure any remote access to the devices with a VPN or secure remote access solution. Unitronics also patched the vulnerability used in this attack in version 9.9.00 of the affected Vision product.
Industrial cybersecurity firm Dragos identified last month that the threat from the hacktivists for the first time achieved Stage 2 of the ICS Cyber Kill Chain when CyberAv3ngers attacked PLCs used by water utilities across North America and Europe with an anti-Israel message. While hacktivist groups typically conduct distributed denial of service (DDoS) attacks with minimal impact, this attack demonstrated the ability to disrupt OT systems by using unsophisticated methods with weak security controls.
The incident also motivated Team82 to research the attack surface of the UniStream PLC series, Unitronics’ current generation of integrated PLCs and HMIs. Among its feature improvements, the UniStream series includes a native authentication schema that Team82 was able to bypass.
“During our research, we uncovered eight vulnerabilities that not only bypassed the authentication and authorization features in the UniStream PLCs but also were able to chain to gain remote code execution on the device,” Team82 researchers wrote in a recent blog post. “Using publicly available internet scanning services, we identified around 480 internet-exposed and vulnerable UniStream devices. It should be noted that these devices are not preconfigured to be reachable online and that these are configuration mistakes on the part of users, likely opening ports on the device for integrator access or other remote support.”
Team82 privately disclosed these vulnerabilities to Unitronics, CISA, and the Israel National Cyber Directorate, which published an advisory on Unitronics having released an update to its Unistream Unilogic software, fixing multiple security vulnerabilities, warning users to update devices and limit their direct exposure to the internet. The agency urges users to update their Unitronics controllers, make sure these devices are not exposed to the Internet, and include mitigation and remediation information.
Unitronics offers a software suite called UniLogic, an interface for programming and configuring Unistream devices, allowing engineers to dictate its logic.
“In our research, we discovered eight vulnerabilities that not only allow a remote unauthenticated attacker to bypass the authentication requirement for interacting with the PLC, but we also chain some of those vulnerabilities to allow an unauthorized attacker to connect to the UniStream PLC, fully control it, and execute arbitrary commands,” according to Team82 researchers.
They added that to map the possible attack surface and potential damage, “we looked for UniStream devices that expose their management web server to the internet. To do so, we used internet-scanning services such as Shodan.io and Censys.io, which constantly scan the IP range, mapping devices they encounter. In the end, we managed to discover around 480 Unistream devices directly connected to the internet that could be attacked using the vulnerabilities we disclosed to Unitronics.”
The Team82 researchers said that it is “important to note that these devices are not configured out of the box to be exposed online, and directly connecting them to the internet can have risky consequences. Users should not only update devices but restrict remote connections behind a VPN or a secure remote access solution. Team82 was able to use internet-scanning services to discover devices directly connected to the internet, a poor best practice that needlessly exposes many organizations to malicious remote connections.
CERT IL, meanwhile, has several mitigation recommendations including calling upon organizations to update Unistream UniLogic software to version 1.35.227 or later. It also recommends that PLCs not be directly connected and accessible to the internet; VPNs or zero-trust network access devices should be used instead, and default passwords should be changed to longer, more complex passwords with two-factor authentication should also be implemented.










