Malware activity surges, threatening OT and IoT environments with nation-states, criminals, hackers
Malware activity and alerts on unwanted applications increased dramatically in OT and IoT environments as nation-states, criminal groups, and hacktivists continue to target healthcare, energy and manufacturing, according to latest research data released by Nozomi Networks.
Increased process automation all over the world is creating new challenges for OT environments, especially where OT systems have limited security visibility and are increasingly expected to be or become interoperable with existing enterprise IT systems, while the addition of new IoT deployments, various sensing capabilities, transient devices, additional networks, and business integrations are also adding new attack vectors and expanding the traditional threat landscape.
In its report, titled ‘OT & IoT Security Report: Unpacking the Threat Landscape with Unique Telemetry Data,’ Nozomi revealed that ransomware continues to plague businesses of all sizes and sectors across the globe. “Healthcare, energy, and manufacturing continue to be targeted by nation-states, criminal groups, and hacktivists. Threat groups like REvil are now tinkering with the potential to combine autonomy, machine learning and natural language models into emerging technologies.”
Describing the report, Chris Grove, director of cybersecurity strategy at Nozomi Networks said in a media statement that there is good news and bad news in this latest report. “A significant decrease in activity per customer in categories such as authentication and password issues and suspicious or unexpected network behavior suggests that efforts to secure systems in these areas may be paying off. On the other hand, malware activity increased dramatically, reflecting an escalating threat landscape. It’s time to ‘put the pedal to the metal’ in shoring up our defenses,” he added.
Nozomi identified that the number of vulnerabilities discovered in OT and IoT devices remains high, many of which are considered critical and/or easily exploitable. Increased process automation all over the world is creating new challenges for OT environments, especially where OT systems have limited security visibility and are increasingly expected to be or become interoperable with existing enterprise IT systems. The addition of new IoT deployments, various sensing capabilities, transient devices, additional networks, and business integrations are also adding new attack vectors and expanding the traditional threat landscape.
The report also revealed that meanwhile, newly discovered and disclosed CVEs (common vulnerabilities and exposures) in both hardware and software components are reported weekly, many of which impact multiple sectors that own and operate similar vendor systems and technologies. It also identified that even when IT attacks don’t cross into OT systems, too often OT networks and processes are hampered by attacks on the IT systems they’ve come to rely upon.
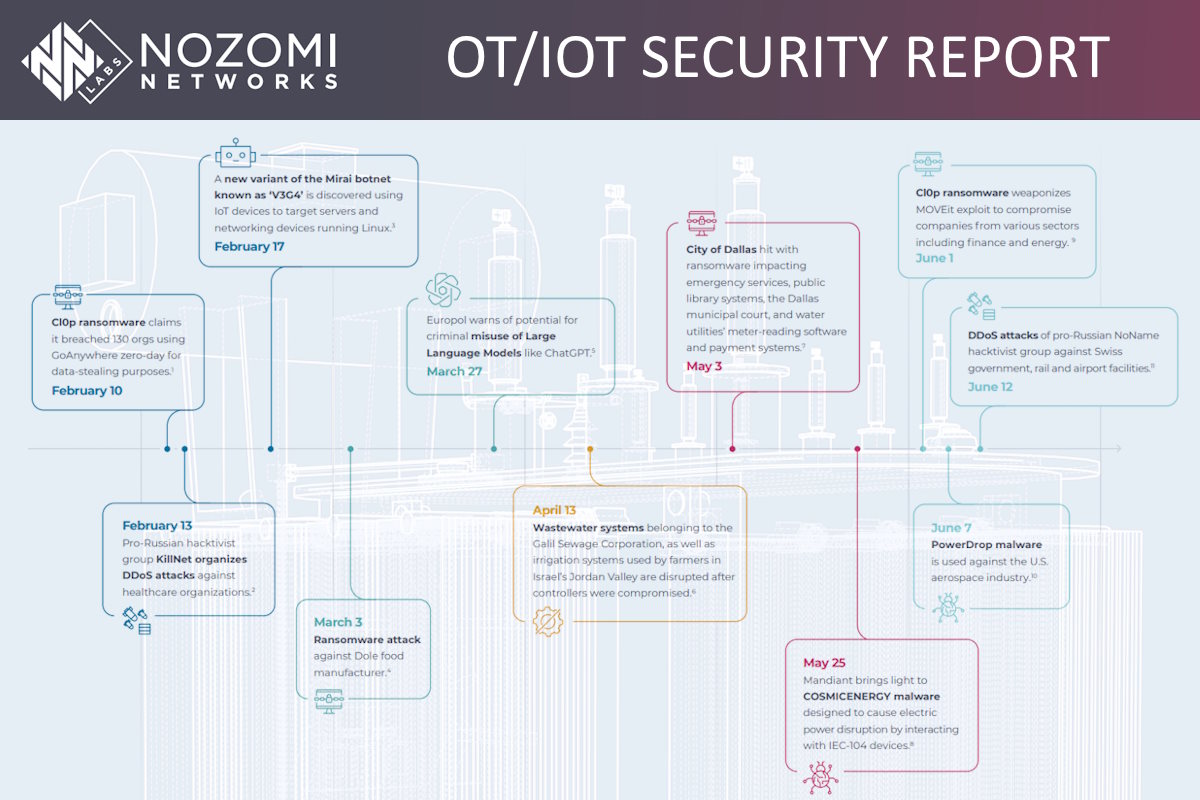
In addition to ransomware, Nozomi identified that DDoS (distributed denial of service) attacks emerged as well as new variants of the 2016 Mirai botnet. Industrial control systems (ICS) were directly impacted in at least three of the incidents in this time period.
Governments around the world have been working to enhance cybersecurity legislation and critical infrastructure policy at the national level in the first half of the year, including the U.S. National Cybersecurity Strategy and its subsequent implementation plan, the European Union NIS 2 Directive, and the Security of Critical Infrastructure Act in Australia.
Nozomi observed in the report that as critical infrastructure attacks continued to make news headlines in the first half of 2023, “governments around the world were adding enhanced cybersecurity legislation and critical infrastructure policy at the national level. New attention is being paid to securing sectors that are integral to the economy, health and human safety, and national security,” it added.
The report also identified that ransomware activity remained strong in the first half of this year, with dozens of threat actors claiming hundreds of new victims based on the publicly disclosed incidents that it reviewed.
“At the time of writing, the most impactful ransomware event this year was orchestrated by the Cl0p ransomware gang (also known as TA505). Cl0p continues to exploit the CVE-2023-34362 vulnerability in MOVEit Transfer software, with the first known exploits deployed at the end of May,” Nozomi reported. “Since then, the list of victims has grown daily and includes U.S. government agencies, oil and gas giants, several banks, media companies, and universities.”
The report added that the ransomware group has been adding new victims at a rate of 13 to 14 victims per day and seems to be far from finished. “In February, the same group compromised multiple companies targeting a different vulnerability in GoAnywhere software. On June 16, the U.S. government offered a US $10 million reward for information that could link the gang to critical infrastructure attacks conducted while operating under the direction of any foreign government.”
Nozomi said that LockBit has been one of the most active and prolific Ransomware-as-a-Service (RaaS) groups in 2022 and 2023. “The LockBit RaaS is so widespread that it accounts for 10% to 25% of all ransomware attacks, depending on the country.16 LockBit’s threat actors have consistently refined and adapted their ransomware strain to infiltrate Linux, VMware ESXi, and Apple macOS systems. This persistent and swift innovation serves as a stark reminder that organizations must maintain constant awareness and exercise vigilance to minimize potential risks,” the report added.
The report also covered the ALPHV group, also known as BlackCat, is another popular RaaS that made headlines in early 2022 when the FBI covered them in a Flash Alert as the first ransomware group to successfully compromise its victims utilizing RUST as a main programming language.
According to Nozomi, healthcare is an attractive target for threat actors due to its lucrative business models and an increasing number of connected devices and assets involved in its operations. At the same time, cyberattacks across the healthcare sector are increasing in frequency while the attack surface for facilities and organizations continues to grow. It is worth mentioning that the vast majority of healthcare organizations heavily rely on legacy equipment, which refers to outdated or no longer maintained equipment. This reliance on legacy equipment poses the highest risk factor for the industry.
Nozomi also assessed the growing community working on generative AI models and exploring their capabilities making these tools widely available to the general population. These new AI systems can be used to automate processes and help cybersecurity defenders with various tasks including phishing email detection, code generation and debugging, grammar reviews, and text translations.
“With these advances in research and innovation, more and more companies are employing AI tools to automate workflows,” Nozomi reported. “As an example, hundreds of industrial and critical infrastructure organizations today benefit from machine learning capabilities in Nozomi Networks solutions to automate and speed alerting and reporting for stronger defenses.”
Analyzing the ICS advisories released by the U.S. CISA (Cybersecurity and Infrastructure Security Agency) between Jan. 1 and Jun. 15, 2023, Nozomi said that the CISA reported 171 new advisories detailing 641 vulnerabilities affecting various products from 62 different vendors, a slight drop compared to 70 in the previous period. Furthermore, critical manufacturing continues to be the most vulnerable standalone sector.
Energy comes in second, followed by water and wastewater, while two new vulnerable industries, food and agriculture, and chemicals, have moved into the top five. Transportation vulnerabilities have dropped to ninth place, falling from their previous position in the top five. Additionally, in the first six months of 2023, healthcare vulnerabilities, which ranked fourth in Nozomi’s previous six-month reporting period, have dropped out of the top 10 rankings.
In its conclusion, Nozomi acknowledges that while security by design is another hot-button security topic today, it won’t solve existing vulnerabilities in deployed technologies. “Targeted attacks will tailor exploitation to a specific, well-researched victim organization, location, or both. Threat actors will continue to pursue living-off-the-land techniques to evade security and extend their reconnaissance efforts to increase the severity of potential exploitation, disruption, and/or damage. Finally, accidental impacts – human error or attacks slipping out of scope to impact OT and IoT – though not always publicly reported, are still fairly common and will become more costly as interoperability continues to drive organizational missions and business decisions,” it added.
It added that vulnerability management, hardening systems, limiting privileged access, practicing proper network segmentation, isolating and testing transient devices, logging events for security analysis, limiting remote access, and planning for robust incident response and operational resilience involving stakeholders at every level of an organization are continued recommendations to prevent worst-case cybersecurity scenarios.










