Prioritizing Your Organization’s Industrial Secure Remote Access


In the past, operational tasks were done by visiting customer sites, however, nowadays, remote access to the OT environment is preferred due to its cost and time efficiency. Of course, remote access is nothing new, but it has now become a universal requirement for industrial enterprises—as has ensuring that all remote access is safe and secure and can’t be exploited or abused by malicious actors, both external and internal. Thankfully, there are ever-advancing technologies to handle the unique complexities of OT environments and the threats they face, however, all industrial organizations must know their current remote access maturity level to ensure greater securityー something TPR can help you with! Keep reading to find out how.
View: Introducing TPR’s Decision Point Industrial Secure Remote Access Report
What is Industrial Secure Remote Access?
Industrial Secure Remote Access typically employs a number of different security strategies to enable users to connect to IT and OT assets from any location, at any time. Solutions were initially designed to provide connectivity to digital IT assets, while OT assets remained sequestered and air-gapped from corporate LANs. When OT networks began to adopt Internet connectivity and remote services, they typically applied IT-type solutions that were already in use elsewhere in the company. To date, numerous industrial enterprises still rely on solutions that were designed for IT and therefore, not tuned to the specific needs of OT/ICS operations, administration, and security. Luckily, today’s cybersecurity market offers a number of I-SRA solutions that are purpose-built for industrial networks.
Why is it important to have remote access solutions designed for OT environments?
Because cyberattack methods improve on a daily basis and are becoming much more sophisticated at finding and exploiting the vulnerabilities of remote access implementations that have not kept pace with the evolving threat landscape. It’s also important to note that remote access implementation is not the same across all industrial sites or for all external parties. As a result, industrial enterprise stakeholders should be aware of their current position on the solution maturity spectrum for I-SRAーmore on that later.
What are the risks associated with Industrial Secure Remote Access?
Remote connectivity creates its own set of threat vectors that must be secured, monitored, and managed. Common pitfalls that continue to plague remote access include:
- Open doors
Insiders and vendors may have an open access port and even a shared password to operate OT assets from an external location. When coupled with basic authentication and little or no monitoring, it leaves the enterprise open to insider abuse and external attack.
- Backdoors
Early implementations that lack monitoring and admin capabilities are notorious for leaving gaps and backdoors open and publicly exposed. An example would be if remote connections are not decommissioned immediately upon cessation of activities and are left open, sometimes indefinitely, allowing for an attack.
- The use of different protocols
Remote services, access points, and methodologies use a variety of access and communication protocols. When a non-integrated mix of technologies is used, it’s almost impossible to enforce a uniform policy or adequately secure all remote connections.
- Compromised credentials
If valid user credentials (whether weak or strong) are shared outright by engineers or captured by bad actors, then adversaries can “walk right in” to OT/ICS operations. Too much trust and too little authentication leave OT networks vulnerable to infiltration.
- Remote access as an attack vector
According to the MITRE ATT&CK knowledge base, adversaries have several ways to gain access using remote methods. They exploit software vulnerabilities in public-facing applications and remote services as well as internet-accessible devices that do not have adequate protection. They impersonate users and systems by capturing valid credentials and using them freely. Once inside, adversaries can leverage remote services to move between OT assets and network segments, just like authorized operators and vendors do, as experienced by the Oldsmar Water Treatment Plant.
Secure architectures for industrial enterprises
Many industrial enterprises use The Purdue Model to construct levels of separation between OT and IT networks, and the interrelationships that govern secure data flows between OT and IT systems. Network segmentation, including a DMZ (demilitarized zone), is an integral part of the Purdue Model. To varying degrees, many industrial enterprises built and operate their OT/IT networks and remote access on this architectural model.
What are the Industrial Secure Remote Access methods?
Industrial Secure Remote Access methods fall into two overarching categories – Direct Access and indirect Multi-Step Access via the I-DMZ. While remote access via the I-DMZ is the more secure method and has been implemented to some degree by almost all enterprises, many industrial environments continue to use Direct Access methods for a variety of reasons.
Direct Access (bypasses the I-DMZ)
Direct Remote Access utilizes three primary methods:
- Dedicated Internet Communication Dongle (often left on site, ready for the next time it is needed).
- Remote Desktop utility where users access the network through client software.
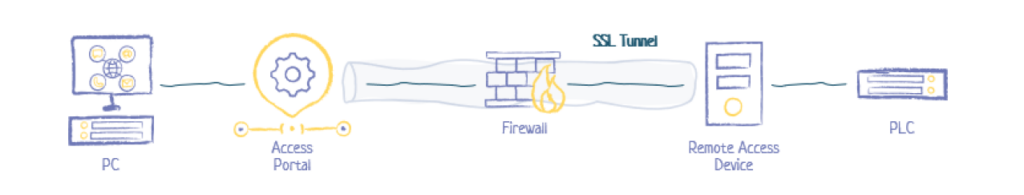
- Direct Internet Applications that use HTTPS or SSH to protect access. These Direct Access applications go through firewalls, routers, switches, and specific control system devices that must keep a port open and remain publicly exposed to enable access.
Multi-step access through the I-DMZ
Most secure remote access, both internal and external, goes through the I-DMZ, which hosts several specialized access systems and protocols for this purpose. Some examples include:
- Jump servers
- Proxy servers
- VPN Tunneling/RDP/SSH Servers
- Internet application direct access
- Zero trust security
Evaluating current I-SRA position and desired goal
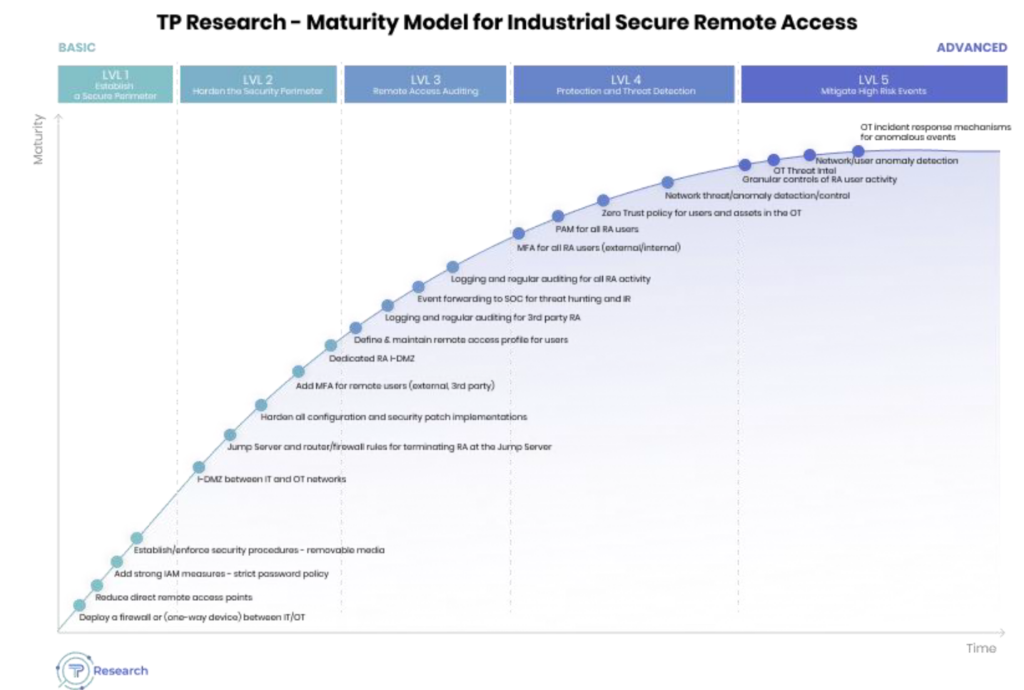
Clearly, there is more than one way to implement Industrial Secure Remote Access to business-critical OT environments. Some are more mature and secure than others, and some are more expensive to implement. To reduce cyber risk, industrial enterprises should periodically evaluate their current I-SRA position vis-a-vis the market solutions that are available and the I-SRA position they would like to be in. It’s hence very important for industrial enterprises to know where they stand on the maturity scale, and whether they need to advance their strategy for Industrial Secure Remote Access.
Identify your current maturity level with TPR
Using TPR’s Decision Point Industrial Secure Remote Access report, you can easily identify your organization’s maturity level using our maturity model, which can be modified to suit each organization and consider the evolving I-SRA landscape. Our report then presents several gradual steps to advance your maturity level that balances I-SRA goals with budgets, complexities, and roadmaps.
Alongside highlighting and improving your maturity level, our report also offers a more thorough breakdown of the I-SRA solutions mentioned above, alongside each one’s maturity level. And it doesn’t end there! We understand how crucial it is to make the right vendor choice(s), so, we also bring you some guidance on recognizing your requirements from vendors and initiating the search.
So, what’s the most important step? The next step. We hope our report helps your organization take the next step toward full Industrial Secure Remote Accessーand on behalf of everyone at TPR, we wish you the best of luck.
We’re so excited to share our TPR Decision Point – Industrial Secure Remote Access report with you that we’re offering a special discount for the first twenty purchased. Secure yours today by clicking here using coupon code: indcybg23.










