ICS-CERT advisories affecting ICS environments show significant increase in 2021
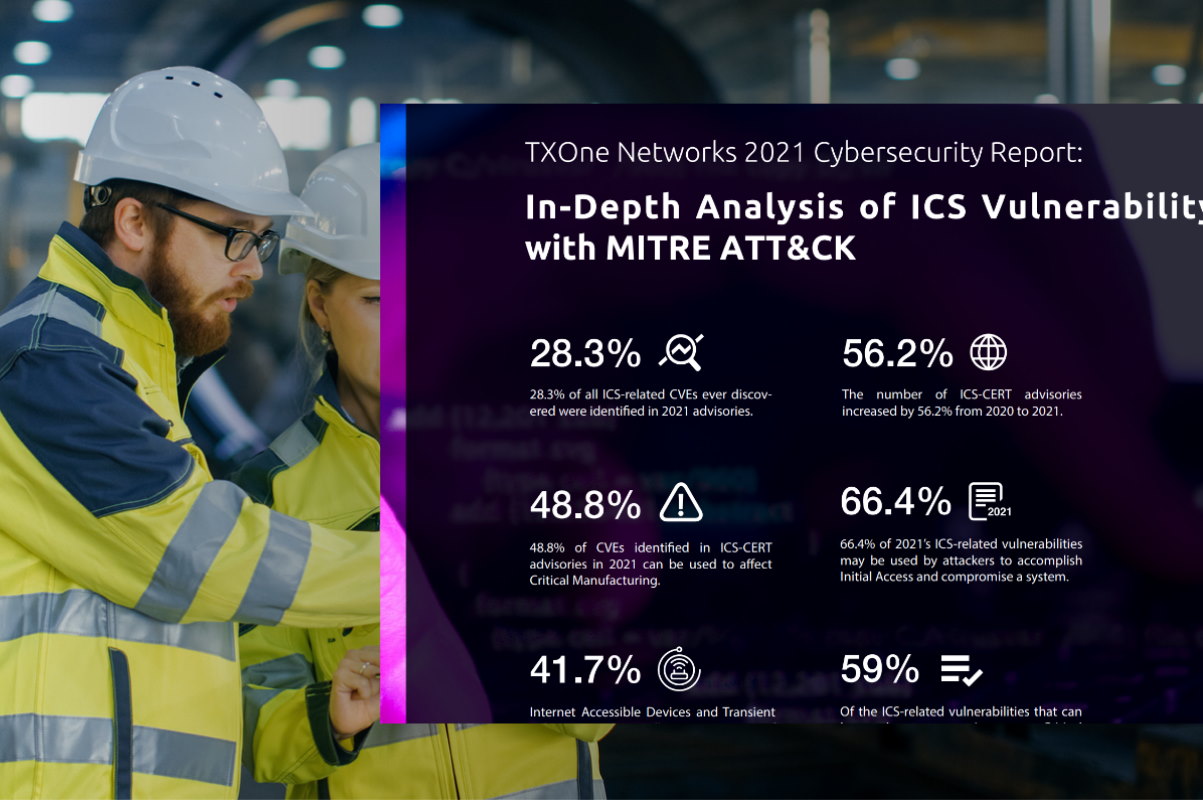
TXOne Networks released on Tuesday its 2021 cybersecurity report that revealed that the number of ICS-CERT advisories dramatically increased in 2021, as attackers have a bigger arsenal to use and launch potential threats in an ICS (industrial control system) environment. The company said that there were 389 ICS-CERT advisories last year, rising from the 2020 figure of 249 advisories, reflecting the largest year-to-year growth in the history of the ICS-CERT program.
TXOne is a company formed by a joint venture of Trend Micro and Moxa, which offers cybersecurity solutions to protect ICS systems and ensure their reliability and safety from cyberattacks.
In its 34-page report, TXOne said that 2021 comes in at 1255 vulnerabilities identified in advisories, or 28.3 percent of the total number of CVEs identified in advisories since 2010. It also revealed how the number of advisories increased year-over-year since the dawn of the ICS-CERT advisory program, with particular spikes in 2017 and 2021. As is typical in recent years, these advisories placed a high focus on security awareness education and on increased cybersecurity preparation. However, the company added that the increasing number of CVEs affecting ICS environments highlights the near impossibility of comprehensively addressing each specific vulnerability.
The TXOne report uses in-depth analysis of vulnerabilities affecting industrial control systems based on MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) for ICS to show current threat and research trends. The company also referenced the Purdue model because it maps an operational technology (OT) environment into layers that can be used to show potential impact.
Each year as vulnerabilities are discovered, they are registered to a Common Vulnerabilities and Exposures (CVE) ID by the MITRE Corp., TXOne said in the report. “Specialists will record the details of each vulnerability and how to mitigate it under this CVE ID. From within those discovered CVEs, those that can affect industrial control system (ICS) environments will be identified to the public through advisories by the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT). By analyzing CVEs identified each year in ICS-CERT advisories, we will show some of the cyber threat and research trends for 2021 and previous years that will affect 2022,” it added.
Based on TXone’s analysis of the 613 CVEs identified in advisories in 2021 that are likely to affect critical manufacturing environments, 88.8 percent of them might be leveraged by attackers to create an impact to directly or indirectly cause varying degrees of disruption to ICS equipment and the environment. For ICS environments, such impact is of critical concern as it could constitute damage or disruption to finances, safety, human lives, the environment, and equipment.
Of those 613 CVEs, 66.4 percent can be exploited to accomplish initial access, which underscores that getting the door open is a major point of interest and surprisingly easy to accomplish in unsecured systems. This can be resisted and made significantly more challenging by applying network segmentation with the zero trust methodology.
Some vulnerabilities require a higher skill level to be used successfully to disrupt operations, while others can be disruptive at a lower skill level, TXOne pointed out. The commonalities of the tactics of execution accounted for 55.9 percent, persistence stood at 55.2 percent, privilege escalation recorded 36.6 percent, evasion observed 48.9 percent, lateral movement accounted for 38.4 percent, command and control stood at 34.9 percent, and impair process control reflected 53.1 percent, indicating that they are much more difficult to accomplish. Attackers and researchers alike discover vulnerabilities that require a lower level to accomplish tactics much more quickly than those that require a higher skill level, it added.
TXOne identified that vulnerability discovery and announcement via advisories is driven by four factors – attackers (which create cyber incidents), governments (which create regulations), organizations (which create rewards and bounties), and vulnerability contributors (which create the research, including discoveries). The number of vulnerabilities addressed by ICS-CERT advisories is a direct indicator of attention that is on the industry, it added.
Another characteristic of 2021 was that it witnessed fundamental changes in the methods favored by cyber attackers, as well as more advanced and destructive supply chain attacks than ever seen before. These new developments in cybercrime have created an environment of anxiety that drives developments in cyber defense and the discovery of ICS-related CVEs.
Looking at a timeline overview of the year’s major OT and ICS cyber incidents shows that modern cybercriminal operations have become so developed that a service industry has emerged with a common business model – Ransomware-as-a-Service (RaaS), TXOne said. Service operators providing RaaS maintain a customizable platform that they offer to users who want to carry out criminal projects. They sell their services using different payment models, including affiliate programs that offer special deals.
TXOne pointed out that recently-active known ransomware groups include Maze, Lockbit, REvil, and DarkSide, though their activity levels can vary. The Maze ransomware group, for example, announced its retirement in November 2020. Around the middle of 2021, REvil and DarkSide got on the U.S. government’s bad side when their service was used to trigger two of the most severe ransomware attacks of 2021, the Colonial Pipeline cyber incident and the Kaseya supply chain attack.
The Colonial Pipeline attack, which resulted in a USD $4.4 million payout to attackers, was conducted using DarkSide’s RaaS platform. REvil’s service was used to initiate the Kaseya supply chain attack by taking advantage of a ‘zero-day authentication bypass’ vulnerability.
Following the Colonial Pipeline and Kaseya attacks, both DarkSide and REvil went quiet, likely due to increased attention from government and law enforcement organizations, with REvil surfacing again in October. TXOne expects continued development on RaaS, including new RaaS platforms that integrate functionality from previous platforms.
“Our researchers suspect but have not confirmed that BlackMatter is actually the DarkSide group resuming operations under a changed name. Most recently, as of December 2021, Emotet and Conti both have resurfaced using advanced exploitation of the Log4Shell vulnerability to accomplish their goals,” it said. The BlackMatter ransomware includes tools and techniques from the Darkside, REvil, and LockBit 2.0 ransomware families.
Another report predicts that supply chain attacks will continue to be a major trend in 2022, with attackers ratcheting up pressure on stakeholders with the method that has come to be known as ‘quadruple extortion.’ This includes holding the victim’s critical data for ransom, threatening to leak the data and publicize the breach, threatening to go after the victim’s customers, and attacking the victim’s supply chain or vendors, it added.
In its report, TXOne said that U.S. President Joe Biden’s May 2021 Executive Order specifically addressed the rise in supply chain attacks as a major threat to the national infrastructure. With the Executive Order, the U.S. government began putting in place regulations designed to prevent such attacks, and one of the biggest changes among these was creating a mandate for Software Bills of Materials (SBOMs) to be provided for each related exchange. These SBOMs will likely be critical documents in the push to improve industrial cyber defense and prevent supply chain attacks.
“We expect the implementation and standardization of SBOMs to be a central challenge for 2022. SBOMs create a system of accountability that aligns well with the zero trust methodology by comprehensively listing the modules, libraries, and components that make up each piece of software or firmware, as well as the related supply chain relationships,” according to TXOne. Any time a vulnerability with the potential to put operational environments at risk is found cyber defense specialists can use the information in an SBOM to investigate and address it, it added.










