Pennsylvania lawmakers push for DOJ investigation into Aliquippa Water Authority cyberattack
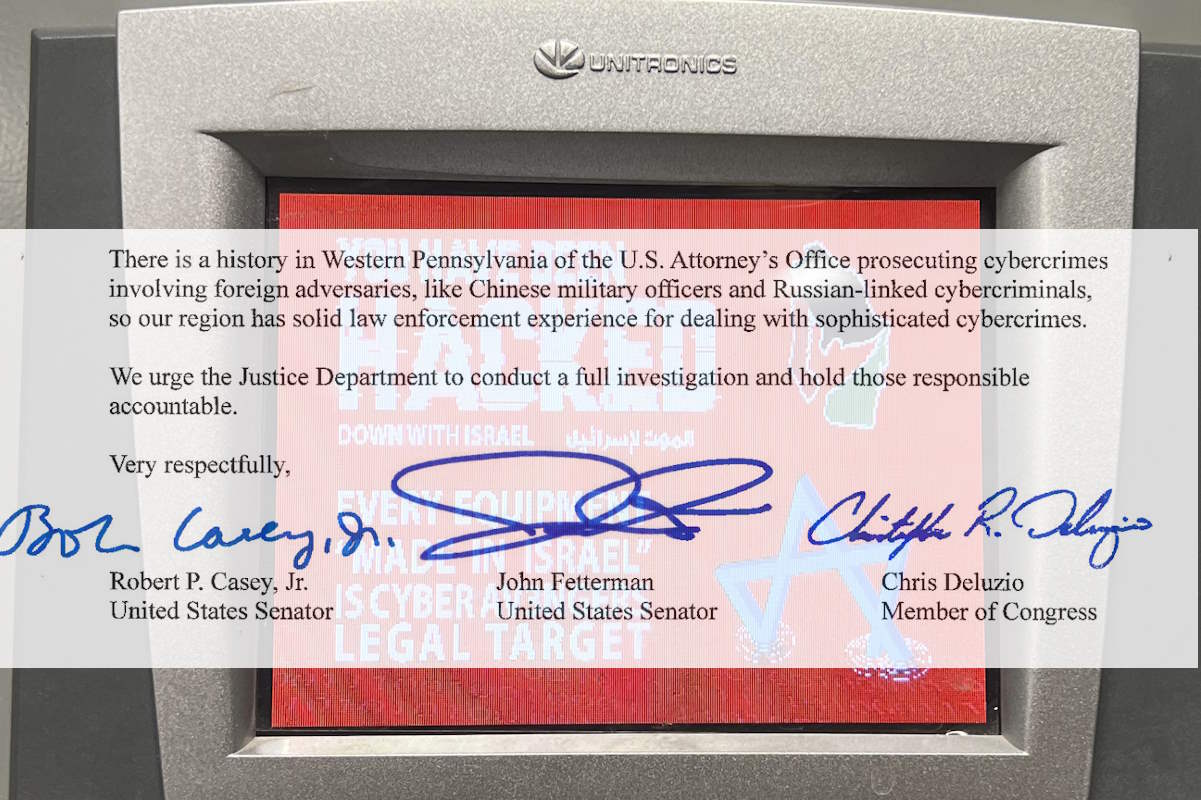
Members of the U.S. Congress called upon the Department of Justice (DoJ) to request a thorough investigation into the recent cyberattack on the Municipal Water Authority of Aliquippa. The Pennsylvania lawmakers are urging a federal inquiry into the attack carried out by the Iranian-backed hacker group CyberAv3ngers, targeting the constituents of the Municipal Water Authority of Aliquippa. They are also calling for ‘aggressive prosecution’ of the attackers.
In a recent letter to Attorney General Merrick Garland, Congressman Chris Deluzio, a Pennsylvania Democrat representative, and U.S. Senators Bob Casey and John Fetterman, both Democrats from Pennsylvania, sent a letter identifying that ‘any attack on our nation’s critical infrastructure is unacceptable.’
The lawmakers urged the DoJ to pursue legal action against the perpetrators, highlighting their concern that this cybercrime not only endangers Western Pennsylvania but also poses a national security threat. The attack, allegedly carried out by an Iranian-backed hacker group CyberAv3ngers targeted the Israeli-made components of the water system that provides service to numerous households serving the City of Aliquippa and Raccoon, Potter, and portions of Hopewell Townships in Beaver County.
“We know that nation-state adversaries are targeting the weakest link in America’s critical infrastructure,” the lawmakers wrote. “We must ensure that our state and local governments, along with private companies, have cyber-defenses strong enough to fend off attacks from sophisticated actors. In Congress, we are committed to pushing our federal government to help shore up our defenses across our critical infrastructure.”
The letter pointed out “If a hack like this can happen here in Western Pennsylvania, it can happen elsewhere in the United States. Folks in Pennsylvania and across the country deserve peace of mind that basic infrastructure such as their drinking water is safe from nation-state adversaries and terrorist organizations.”
The lawmakers also pointed out that there is a history in Western Pennsylvania of the U.S. Attorney’s Office prosecuting cybercrimes involving foreign adversaries, like Chinese military officers and Russian-linked cybercriminals, ‘so our region has solid law enforcement experience for dealing with sophisticated cybercrimes.’
Over the weekend, the U.S. Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Environmental Protection Agency (EPA), and the Israel National Cyber Directorate (INCD) jointly released a Cybersecurity Advisory (CSA). The advisory draws attention to ongoing malicious cyber activity targeting OT devices. Specifically, the advisory focuses on the actions of Advanced Persistent Threat (APT) cyber hackers affiliated with the Iranian Government’s Islamic Revolutionary Guard Corps (IRGC).
The U.K. National Cyber Security Centre (NCSC), which is a part of GCHQ, is recommending organizations follow the U.S.-Israel guidance regarding the active exploitation of Unitronics programmable logic controllers (PLCs) used across industries, including the water, energy, food and beverage, manufacturing, and healthcare sectors.
“The NCSC has warned for some time of the enduring threat to the UK’s critical national infrastructure,” Jonathon Ellison, NCSC director for national resilience and future technology, said in a media statement. “Our international counterparts have issued an advisory outlining a threat against a range of industries, including the water sector.”
Ellison added that the NCSC is “notifying UK providers of this threat, and recommend they protect consumers by following the mitigation advice set out in the advisory.”
Commenting on the Aliquippa attack, Chris Grove, director of cybersecurity strategy at Nozomi Networks, wrote in an emailed statement that “Observing how a cyber-attack on critical infrastructure, motivated by nation-state, hacktivist, or terrorist agendas, is triggered merely by the presence of equipment from a specific country, marks a new frontier of risk for skeptics.”
He added that this incident “should be a wake-up call, emphasizing that no entity is immune to cyber-attacks, regardless of their operation’s nature, scale, or location. Today’s digital landscape, especially in critical infrastructure sectors, is akin to a modern battlefield. Whether we acknowledge our involvement or not, our mere presence in this arena entails significant risks.”
Before the compromise of these devices, the CyberAv3ngers stated they were planning to attack Israeli technology companies, Mark Plemmons, senior director for threat intelligence at Dragos, wrote in an emailed statement. “They likely scanned the open internet to identify publicly accessible Unitronics devices and then attempted to log into the devices using the Unitronics default password setting which can be easily found online.”
“The silver lining is that the CyberAv3ngers hacktivist group does not possess specific OT capabilities, so the intrusion only resulted in the PLC devices’ main HTML menu page being altered with anti-Israel commentary,” according to Plemmons. “The access gained by these actors remains a concern, however, because other manipulation of the associated systems could be attempted – with unknown consequences that are specific to each environment which uses these devices. However, this incident highlights the importance of basic security fundamentals for any OT system, no matter how small,” he added.
Plemmons added that the CyberAv3ngers more targeted attack against easily discoverable and default-configured PLC devices represents a successful OT attack, though with limited impact on the actual systems and associated processes controlled.
Sagi Berco, CTO at NanoLock Security, wrote that “Securing the operational technology (OT) that controls the water supply, particularly the programmable logic controllers (PLCs), should be the top priority for a water utility’s CISO. And this is where the challenge begins. It’s an extremely difficult task.”
“It’s critical to implement a zero-trust mechanism directly onto these devices. While CISA urges organizations to require multi-factor authentication to the OT network, it should also require MFA to the devices directly,” Berco said. “This approach can prevent unauthorized changes to PLC programming, even in the event of an attack, regardless of vendor or PLC type. Applying zero-trust to level-1 OT devices is crucial in preventing any potential damage to the water supply, as in this case, where citizens’ safety is at stake,” he added.
Christopher Warner, a senior security consultant for OT Security – GRC at GuidePoint Security, emphasized the significance of assessing the security posture of every critical infrastructure organization in response to the Aliquippa water utility hack. “Identifying the assets in place, understanding their vulnerabilities, and conducting a comprehensive program review aligned with a recognized framework, incorporating best practices is crucial.”
Warner added that security is an ongoing process requiring constant diligence to safeguard systems that provide essential services such as energy, water, gas, food, healthcare, and more.
Mark Toussaint, senior product manager and OT expert at OPSWAT highlighted that mitigating cybersecurity risks in ICS systems can present a challenge for some organizations. This is especially true for smaller municipalities that oversee water and wastewater systems, as they often have limited resources available.
“This industry is also not regulated by enforceable cybersecurity requirements, making it more vulnerable,” according to Toussaint. “However, alignment with other industry best practices for OT environments is a great first step, along with a foundational approach. Identifying threat vectors and implementing solutions to reduce the likelihood of impactful attacks, such as controlling removable media in secured environments, are essential components of this strategy.”
Toussaint added that given that critical infrastructure sectors like water and wastewater are increasingly targeted by nation-state threat actors seeking to cause disruption, it is crucial for organizations to stay ahead of the curve. “We know the White House has initiated executive orders and national plans to bolster cybersecurity, and industry-specific regulators are publishing cybersecurity guidelines, but in the face of evolving cyber threats, it is imperative for organizations to take a proactive and comprehensive perimeter defense strategy.”










