NSA information sheet focuses on enhancing data security and zero trust implementation
The U.S. National Security Agency (NSA) is offering guidance to enhance data security and protect data both at rest and in transit. The recommendations in the Cybersecurity Information Sheet (CSI) focus on limiting data access to authorized individuals. The CSI emphasizes the importance of the data pillar and its capabilities in reducing risks through encryption, tagging and labeling, data loss prevention strategies, and the use of data rights management tools. These capabilities outlined in the CSI are in line with a comprehensive Zero Trust (ZT) Framework.
Titled ‘Advancing Zero Trust Maturity Throughout the Data Pillar,’ the information sheet provides recommendations for maturing data security and enforcing access to data at rest and in transit, ensuring that only those with authorization can access the data. It further discusses how these capabilities integrate into a comprehensive ZT framework.
“Traditional security approaches have often relied on perimeter defenses alone to secure networks. Recent events highlight that adversaries who are successful at gaining a foothold in information systems often readily gain unfettered access to all data in those systems,” the information sheet detailed. “By applying the recommendations in the data pillar, including identifying risks to data, integrating granular data attributes into access control mechanisms, and monitoring data access and use, organizations will reduce the impact and consequences of breaches and identify suspect activity earlier in the cyber intrusion lifecycle.”
It added that to protect data, an organization needs to know what data it has and track how it moves and is accessed inside and outside the enterprise. “Tracking data can be a significant task, so having an automated method for identifying data of value on the network or performing a data inventory operation is recommended. Data protection ensures that data is only accessed by authorized entities.”
The information sheet also detailed that granular control of data not only keeps it safe within the enterprise but also ensures that it can be safely shared with other organizations and partners to achieve interoperability. Implementing these activities will limit the ability of adversaries to reach targeted data assets. It will also provide visibility to system managers of compromised assets that require mitigation should adversaries be successful in their efforts.
“Malicious cyber actors continuously increase their ability to infiltrate networks and gain access to sensitive data,” Dave Luber, NSA’s director of cybersecurity, said in a Tuesday media statement. “Assuming that breaches will occur, implementing the pillars of the Zero Trust Framework is how we combat that activity. Data pillar capabilities verify all access to data — one of the key foundational elements for building improved cybersecurity — thereby reducing the impact of breaches and enabling earlier detection of even advanced malicious cyber actor activities.”
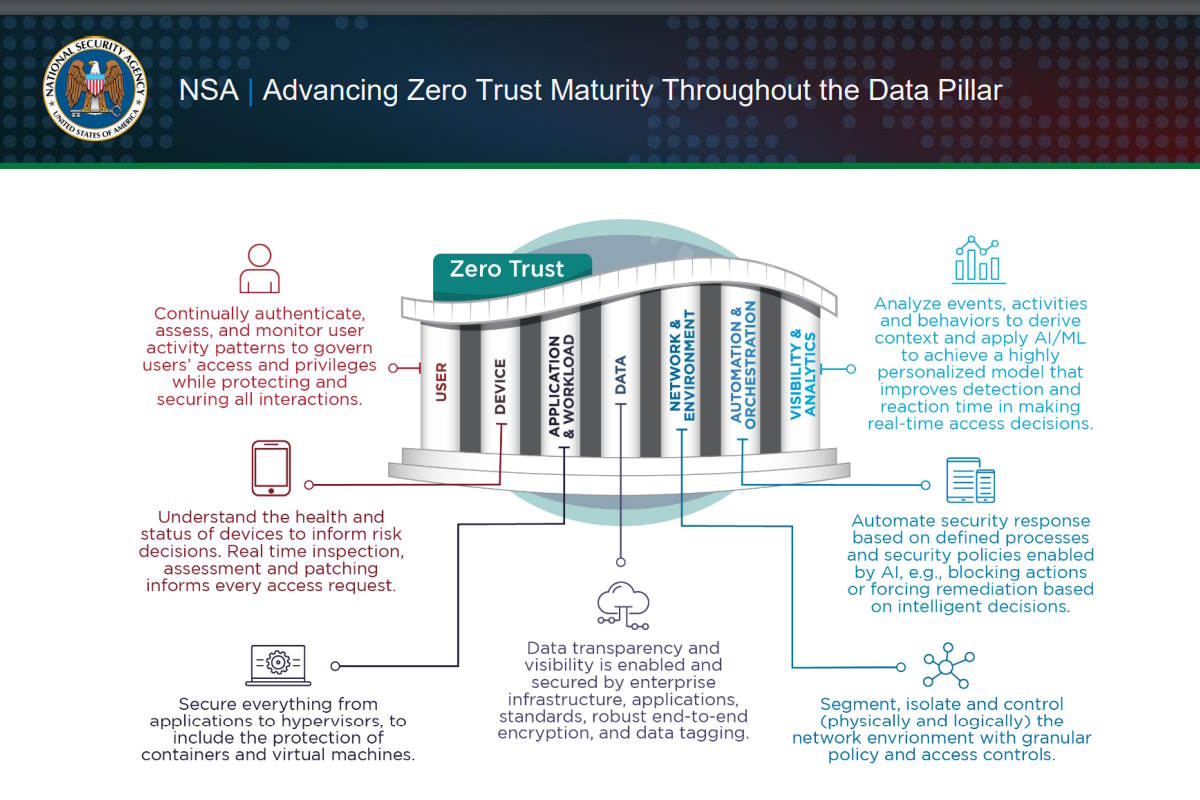
Since releasing the ‘Embracing a Zero Trust Security Model’ Cybersecurity Information Sheet in February 2021, the NSA has continued to release updates and related products that guide how to adopt a ZT mindset to secure systems. The seven pillars of ZT architecture are as follows: user, device, network/environment, applications and workload, visibility and analytics, automation and orchestration, and data.
The latest information sheet recognizes that adopting ZT principles is not accomplished overnight. Implementing them is achieved through careful and deliberate planning and continuous incremental improvements that bring cybersecurity protections, responses, and operations to maturity over time.
Building capabilities aligned to a mature ZT framework requires integrating every system in the enterprise with the appropriate security controls, best practices, configuration management, and vulnerability management for each of the seven pillars: User, Device, Network and Environment, Data, Application and Workload, Visibility and Analytics, and Automation and Orchestration. Each pillar constitutes a key focus area of ZT implementation, with the data pillar effectively secured by the other six.
The first step in controlling data against threats is to identify all types of data in the environment and assess their risks of exposure, loss of availability, and loss of integrity. An enterprise data catalog should be a comprehensive inventory of data within the enterprise available for reference. This catalog, while not containing the data itself, includes metadata about the data, governance policies, and data usage.
Data owners within an organization are aware of the details and purpose of their data. They must ensure their data is identified, inventoried, and categorized in the data catalog. This enterprise view of the data helps to facilitate data governance activities. When data owners review the catalog, they can identify potential risks or risk levels related to data loss, breach, or any other unauthorized alteration and/or access to data.
It also detailed that enterprise data governance ensures that data is controlled, accessed, and shared across organizations according to defined policies based on inputs from their cybersecurity infrastructure. Enterprise data labeling and tagging, access control, and sharing policies, along with Data as a Service (DaaS) capabilities, where applicable, ensure enforceability at the data object level.
The information sheet also sought to establish granular data attributes integrated into access control systems consistently and correctly is required for machine-enforceable data access controls, risk assessment, and situational awareness. As data attribute tagging and labeling practices mature, labeling should become automated to meet scaling demands and provide better labeling accuracy.
It also recognized that organizations should apply granular attributes to security and mission-critical data on high-value assets first. Organizations should tag data in accordance with enterprise policies. Phases of implementation should advance toward full automation to enable accurate tagging at scale. Once data is properly labeled and tagged, the organization should establish automated data access controls, risk assessments, and monitoring for situational awareness based on enterprise governance policies.
Data should always be detectable and observable by those who should have access to it and those who are required to manage it. Data metadata should be observable for tracking and alerting, although sometimes only partially since metadata can have sensitivities and access controls. Data owners and automated management solutions should ensure all data has associated metadata that includes current information about the access, sharing, transformation, and use of the data assets.
The information sheet highlighted that data encryption and rights management combines technology with policy to protect data against unwanted access, modification, or redistribution. Data should be automatically encrypted based on data attributes assigned through tagging and labeling. By encrypting the data, organizations can be more assured their data is protected even if it is exfiltrated or lost as long as a malicious actor does not have the associated decryption keys.
Furthermore, organizations must establish a baseline for data usage before enabling the prevention capabilities of DLP tools. When implemented correctly along with the other capabilities of the data pillar, DLP tools, established throughout an organization’s network and not just at the perimeter, can more reliably secure an organization’s data.
Insider threats can pose a great risk to an organization. Entities with access to sensitive data from within can leak, destroy, or steal that data, intentionally or unintentionally. For example, a vexed former employee could steal data to sell to a competitor, or one might accidentally leak sensitive data by using it in an AI tool, such as a large language model (LLM). DLP can help stop the unauthorized forwarding, copying, or destruction of sensitive data by tracking sensitive information within the network.
The information sheet also covered data access control that seeks to limit access to and use of data-based properties and attributes associated with the data and a user/device tuple along with any other relevant information. “This capability is dependent on the others and brings into focus the ultimate job of the data pillar to enforce granular access controls and utilize all available data attributes for access decisions. This ensures unauthorized entities or entities on unauthorized devices cannot access the data,” it added.
Furthermore, it also ensures that those users and devices with access to data will continue to have their attributes inspected through various policy decisions and enforcement points within the architecture.
In conclusion, the NSA information sheet underscores the importance of safeguarding data, a vital asset for any organization, which is the core focus of ZT. Data protection is achieved through thorough cataloging, labeling, and encryption both at rest and in transit. ZT’s strategy is ultimately centered on protecting an organization’s data through constant verification, so data owners must take the steps necessary to survey their data to design and implement effective controls.
Once in place, those controls should be tested and the maturity evaluated. Implementing an effective data management plan within the ZT framework will limit data breaches, and if a breach does occur, will provide the necessary information on the assets that were compromised to minimize the damage.
Recently, the NSA issued a cybersecurity information sheet addressing the challenges of implementing hybrid cloud and multi-cloud environments, providing solutions to tackle the increased complexity. The document underscores the intricacies brought about by these environments.










