Zero Trust Network Access (ZTNA) – Revolutionizing remote access security across OT environments

In today’s interconnected global landscape, the need for remote access has become essential. Integrating Zero Trust Network Access (ZTNA) into operational technology (OT) environments signifies a notable shift from traditional methods like virtual private networks (VPNs) and dedicated cellular gateways. ZTNA, with its least-privileged model, enhances security by allowing specific access based on user identity and necessity, minimizing the exposure of the entire network.
ZTNA enhances security by adopting a ‘never trust, always verify’ approach, ensuring that remote users can only gain access to applications and systems they are authorized to access. The model primarily works towards reducing the attack surface and minimizing the risk of wide open access to resources. Its application in the OT landscape addresses traditional challenges like remote site connectivity.
Additionally, ZTNA facilitates continuous monitoring and adaptive risk assessment, empowering dynamic adjustments to security postures. As industries recognize the importance of securing OT assets, the adoption of ZTNA emerges as a pivotal strategy, ensuring a robust defense against evolving cyber threats targeting critical infrastructures.
Drawbacks of traditional remote access solutions

Ruben Lobo, director of product management for industrial IoT at Cisco, highlighted the limitations of traditional remote access solutions in OT environments in a conversation with Industrial Cyber. He pointed out that VPNs installed by IT teams in the industrial DMZ (IDMZ) are always-on solutions with all-or-nothing access to OT assets. Controlling who has access to what requires using jump servers to manage sessions and complex firewall rules that need to be frequently updated to prevent wide-open access.
Lobo noted that “The Colonial Pipeline cyberattack is an example of a breach caused by VPN neglect. Hackers breached the system using an orphaned VPN account that was no longer in use and not protected by multi-factor authentication (MFA).”
“Managing and enforcing access policies across multiple sites in a VPN architecture can become a daunting task, especially in OT environments where assets are so numerous and remote users generally work for third parties,” Lobo said. “This complexity and the fact that jump servers are installed in the IDMZ explain why VPN access is commonly maintained by a separate entity in the organization, which can cause delays for vendor connectivity and impact operational agility or even production uptime.”
Looking into how maintenance windows and uptime requirements in OT systems exacerbate the challenges of traditional remote access solutions, Lobo pointed to the fact that uptime and safety are paramount in industrial networks. “Maintenance activities need to be carried out at very specific times and often need precise planning to avoid disruptions. For example, closing a pipeline outside a maintenance window or shutting down a conveyor belt while the assembly line is still working could be catastrophic. Safely powering down a furnace and making sure it returns to the right temperature are complex processes that need to be carefully carried out.”
Remote maintenance and troubleshooting in production infrastructure often involve external entities, making it crucial to control their access and prevent unrestricted entry. Enforcing access control policies with VPN-based solutions can be quite complex and needs support from the IT team. Cellular gateways or remote access software installed by machine builders or maintenance contractors make it very difficult to control who is connecting, what they are doing, and what they can access.
Benefits of Zero Trust Network Access (ZTNA) approach in OT
As OT folks are rather skeptical of the latest IT/cybersecurity buzzwords, Lobo weighs in on the key principles of ZTNA and their implications for OT, while also separating fact from fiction. “Cellular gateways or remote access software that IT is not controlling are at odds with the OT security projects undertaken by the IT/CISO teams and create a shadow-IT situation that is putting the industrial network at risk. The operational overhead of deploying VPN solutions with all the necessary security checks and controls often leads to lackluster policies and wide-open access policies. The critical need for remote access to OT assets calls for a better security solution,” he added.
Lobo approaches ZTNA as a mature technology increasingly adopted in enterprise networks to facilitate hybrid work and secure access to resources, regardless of where apps and users are located. He explains that ZTNA is a security service that ensures strong users’ authentication and grants access to specific resources at particular times, based on identity and context policies. This approach begins with a default deny posture and adaptively provides the necessary trust level as required.
“Remote employees, vendors, and contractors connect to a ZTNA trust broker, typically a cloud service where they are authenticated and offered access only to the devices you choose, using only the protocols you specify, and only on the day and time you allow,” explained Lobo. “The trust broker communicates with a ZTNA gateway deployed in the industrial network responsible for creating a communication path to the OT assets. With this architecture, assets are hidden from discovery, and lateral movement is restricted. MFA, single sign-on (SSO), and security posture checks are enforced by the trust broker which also centralizes access policies for all assets across all sites.”
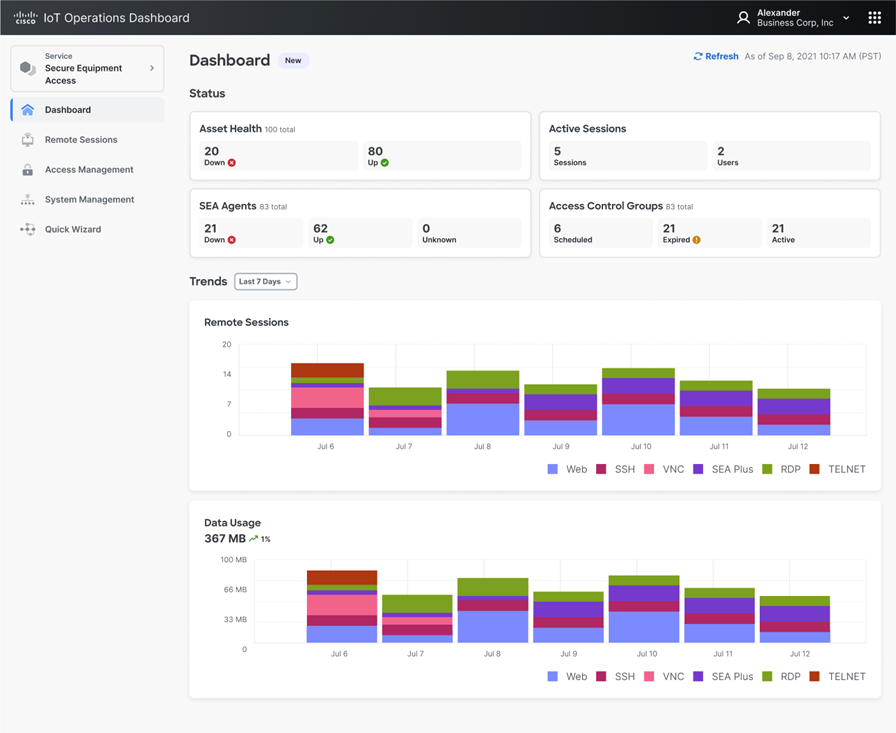
The ZTNA trust broker simplifies OT/ICS remote access management by centralizing policy definition and offering global visibility and control on all remote access sessions.
Addressing how exactly the ZTNA model enhances security in OT environments, Lobo commented that the model enforces the least-privilege principle commended by the ISA/IEC 62443-3-3 security standard: remote users only have access to the resources they need to do their job.
“We need to differentiate between zero-trust network segmentation and zero-trust network access. Both solutions start with a default deny posture. In a zero-trust segmentation architecture, assets are only allowed to communicate with those they need to run the industrial process,” Lobo observed. “This is what the ISA/IEC 62443-3-3 security standard recommends by proposing a zones and conduits architecture. It’s the role of the industrial network to enforce this zone segmentation by restricting communications as defined in security policies.”
“ZTNA extends this ISA/IEC 62443-3-3 least-privilege principle to remote access use cases,” said Lobo. “As more assets are connected, more third-party experts and contractors are getting involved remotely. They should be granted only the rights they need to perform their work.”
Cisco recently introduced a ZTNA solution specifically designed for OT workflows called Secure Equipment Access (SEA). “Cisco SEA is a cloud service that works with Cisco industrial network equipment to make this very simple to deploy at scale in an OT environment,” according to Lobo. “It enables granular access policies and offers a seamless user experience, advanced security controls, while empowering OT administrators to configure access policies themselves.”
Administrators can configure access policies for each asset and for each user, combining criteria such as schedules, permitting remote access only during specific periods, and access methods, to give remote operators the ability to use only the protocol you selected such as SSH, RDP, VNC, HTTP(S), Telnet, or any UDP, TCP, or ICMP-based application. This ‘just-in-time’ access ensures no remote configuration can be done during production, but only during maintenance windows, for instance.
The ZTNA architecture makes it simpler to configure and manage remote access at scale by centralizing policy configuration in the trust broker rather than distributing it into all jump servers and firewalls deployed across the organization. ZTNA also greatly reduces the attack surface. The trust broker is the single point of entry to the network making it a more challenging ‘moving’ target for hackers as it is based in the cloud.
“Cisco Secure Equipment Access addresses the risk of stolen credentials by enforcing multifactor authentication (MFA),” Lobo added. “It works with identity providers (IDP) for SSO to streamline user experience and enforce strict user policies from a centralized location. It works with Cisco Duo to assess the remote user’s security posture when full IP access to an asset is required.”
The ISA/IEC 62443-3-3 security standard also requires remote access sessions to be traced for audit and compliance purposes. “Cisco Secure Equipment Access gives administrators full control over remote access sessions with the ability to join an active session to see what’s happening and terminate sessions that should never have become active in the first place or in which the remote user deviates from permitted actions,” Lobo detailed. “It also offers the ability to record sessions for use in audit trails and to watch what remote users did to a system to aid incident investigation.”
Why ZTNA for OT networks must be distributed
Addressing the potential limitations of implementing ZTNA solutions for accessing OT assets, Lobo noted that with existing ZTNA solutions, gateways are centralized in the IDMZ. “This centralized architecture puts the ZTNA gateway too far from the OT assets and suffers the same drawback as the legacy VPN design,” Lobo mentioned. “In large industrial sites such as manufacturing plants, IP addresses are often reused, and many assets sit behind NAT boundaries which make them unreachable to the ZTNA gateway in the IDMZ. The complexity now falls on the end customer to expose these private IPs to the higher layers of the Purdue model.”
In field networks such as roadways or utility infrastructures, Lobo noted that installing dedicated ZTNA gateways is often not feasible due to space constraints. “When space is available, having to maintain dedicated ZTNA gateway hardware just to access a few OT assets puts an undesirable burden on customers,” he added.
With Secure Equipment Access, Lobo said that Cisco is solving the challenges of deploying ZTNA in industrial networks at scale. “It embeds the ZTNA gateway function into Cisco industrial switches and routers, making secure remote access capabilities very simple to deploy. There is no point hardware solution to source, install, and manage. Enabling remote access is just a software feature to activate in the Cisco industrial network equipment.”
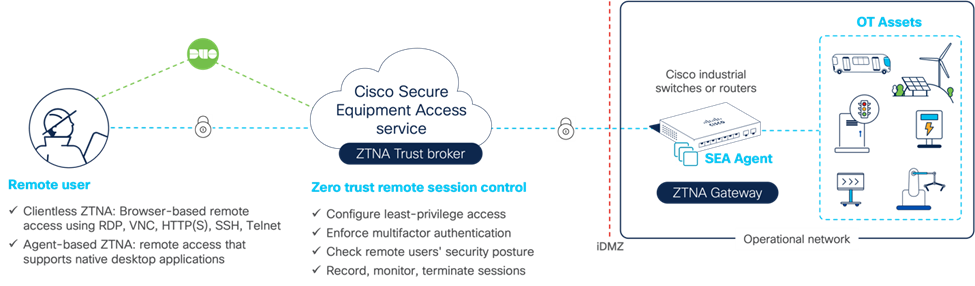
Cisco SEA distributes the ZTNA gateway function in industrial switches and routers to avoid deploying dedicated hardware and be able to reach any OT asset, even those behind NAT boundaries.
“By embedding the ZTNA gateway into the industrial network, Cisco is making OT remote access both more secure and easier to manage at scale,” Lobo outlined. “Distributing the ZTNA gateway function anywhere in the network lets you remotely access every asset. The Cisco industrial switch or router that provides secure and reliable connectivity to OT assets, now also provides zero trust remote access to these assets, whatever their IP addresses or your NAT strategy,” he explained.
With the distributed architecture Cisco has adopted, “enabling remote access to new assets just requires creating a new access policy in the trust broker. OT administrators can now manage access credentials by themselves when needed. Adding OT assets or changing their IP addresses does not require any firewall configuration.”
Additionally, the same network equipment that embeds the ZTNA gateway software can also enforce micro-segmentation policies to prevent lateral movements in the case the asset is used as a jump host. “Only Cisco offers such an advanced security capability in industrial switches and routers today,” Lobo flagged.
In conclusion, Lobo said “ZTNA is not just a feature of remote access solution, it’s an architecture that includes features to authenticate users, verify their security posture, hide assets from discovery, prevent lateral movement, enforce access policies and more.”